Privacy International's Work on Hacking
Introduction
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. Yet hacking presents unique and grave threats to our privacy and security. It is far more intrusive than any other surveillance technique, capable of accessing information sufficient to build a detailed profile of a person, as well as altering or deleting that information. At the same time, hacking not only undermines the security of targeted systems, but also has the potential to compromise the internet as a whole. For these reasons, Privacy International has focused sustained attention on this issue. Below, we describe our legal and policy work to address government hacking.
Our Legal Work on Government Hacking
A. United Kingdom
The Snowden disclosures revealed sweeping hacking operations conducted by the British signals intelligence agency, the Government Communications Headquarters (“GCHQ”), and its American counterpart, the National Security Agency (“NSA”).[1] As a result of those disclosures, Privacy International, together with seven internet and communications service providers, brought a complaint in British court challenging GCHQ hacking domestically and abroad.[2] This case is one of the first to directly challenge the legality of government hacking powers anywhere in the world.
We filed our initial complaint in May 2014 before the Investigatory Powers Tribunal (“IPT”), a specialised court in the UK that hears complaints about surveillance by public bodies, including the British intelligence agencies. Our case argued that GCHQ, which until the Snowden disclosures was hacking in secret, had no legal authority to deploy these capabilities. We further argued that GCHQ hacking violates Articles 8 and 10 of the European Convention on Human Rights (“Convention”), which respectively protect the rights to privacy and freedom of expression.
In February 2016, the IPT rejected our claims. Its decision condoned GCHQ’s use of a broad legal power under section 5 of the Intelligence Services Act 1994 (“ISA”) to authorise domestic hacking and found this power to be compliant with the Convention. The IPT also accepted the government’s position that section 5 ISA authorises “thematic warrants,” which are warrants that can cover an entire class of unidentified persons, places or property. During the proceedings, the government asserted — and the IPT agreed — that it could seek a single thematic warrant to hack all mobile phones in an entire city.
The IPT refused to rule on the legality of GCHQ’s foreign hacking powers, which it conducts in bulk pursuant to section 7 ISA. The IPT’s refusal means these powers also continue unchecked.
We are pursuing two separate challenges of the IPT’s judgment.
In May 2016, we filed a judicial review application at the UK High Court, objecting to the part of the IPT’s judgment that sanctions GCHQ’s domestic hacking powers. A judicial review is a type of collateral challenge to the lawfulness of a decision by a public body. Our challenge focuses, in particular, on GCHQ’s use of thematic warrants, which, as explained above, can encompass an entire class of unidentified persons, places or property. We argue that thematic warrants undermine 250 years of English common law, which is clear that a warrant must target an identified individual or individuals. We also argue that thematic warrants fail to comply with Articles 8 and 10 of the Convention.
In August 2016, we filed an application at the European Court of Human Rights, challenging the IPT’s refusal to determine the legality of GCHQ’s foreign hacking powers. In our application we are joined by five of the internet and communications service providers who litigated the case with us at the domestic level.[3]
B. United States
1. Apple v. FBI
In March 2016, Privacy International, together with Human Rights Watch, filed an amicus curiae brief in In the Matter of the Search of an Apple iPhone Seized during the Execution of a Search Warrant on a Black Lexus IS300, California License Plate 35KGD203 in the US District Court for the Central District of California. Popularly known as the “Apple v. FBI” case, the dispute stemmed from the FBI’s investigation of a December 2015 mass shooting in San Bernardino, California. As part of its investigation, the FBI obtained an iPhone used by one of the deceased shooters. The data on the iPhone was encrypted and the FBI filed an application for an order of assistance under the All Writs Act, 28 U.S.C. §1651, to compel Apple’s assistance in accessing that data. In particular, the FBI sought to compel Apple to design and write custom software that would cripple core security features of the iPhone. [4] The court issued the order, which Apple challenged on the grounds that it was unlawful and unconstitutional.
Our brief focused on the international implications should the Court compel Apple to assist the FBI by hacking its own iPhone. In particular, we discussed how other countries already seek the power to compel technology companies to undermine the security of their products or services, through hacking and other techniques. We argued that should the Court compel Apple to assist the FBI, it would encourage these countries to place heightened pressure on companies to comply. Our brief also touched upon the civil and human rights abuses that can — and have — occurred when governments seek to exploit security weaknesses in technology products and services.
2. FBI Hacking
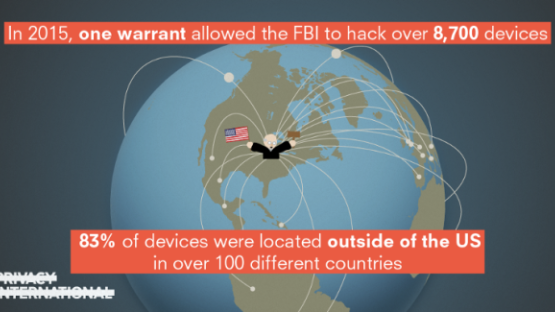
In February 2017, Privacy International filed an amicus curiae brief in United States v. Levin in the US Court of Appeals for the First Circuit. The case is one of a series of criminal cases stemming from an FBI hacking operation conducted in 2015 pursuant to a warrant issued by a magistrate judge in the Eastern District of Virginia. The warrant authorized the FBI to execute a hacking technique — what it calls a “network investigative technique” (“NIT”) — on untold numbers of computers located anywhere in the world. On the basis of this single warrant, the FBI hacked over 8,700 computers, in 120 countries and territories. Over 83% of these computers were located outside the US.
The FBI deployed this hacking technique in order to identify visitors to the child pornography website Playpen. These visitors were accessing Playpen via the Tor network, which protects the anonymity of users browsing the internet. Playpen was a “hidden service” on the Tor network, meaning it was only accessible through Tor. People use Tor and other anonymizing technologies for a variety of reasons, including to prevent websites from tracking them, access websites and services blocked in their respective countries, and send and receive sensitive data, such as financial or medical information.
Our brief drew attention to the international implications of the FBI’s hacking operation. Well-established international law and practice prohibit a state from unilaterally conducting investigative action beyond its borders, in other words, without the consent of affected states, as the government did in this case. The foreign relations risks attendant in such action underlie this principle, for it can be perceived as a violation of sovereignty, with the potential to lead to diplomatic conflict. In the digital realm, unilateral investigative action poses particular risks. As the public is increasingly learning, the nature, scope and purpose of a hack — especially where foreign actors are involved — can be difficult to determine. It can therefore run a risk of being mischaracterized and heightening diplomatic conflict.
Our Policy Work on Government Hacking
A. An International Set of Recommendations
Because of the privacy and security implications of hacking, Privacy International questions whether it can ever be a legitimate component of state surveillance. If governments are to hack, they must bring this activity in line with international human rights law and standards. Privacy International is therefore working to establish a set of recommendations, which are based on international human rights principles, including those set forth in the International Principles on the Application of Human Rights to Communications Surveillance.
In March 2015, we released our first iteration of these recommendations, which were formulated in response to the British government’s release of a draft code of practice on hacking. We are currently in the process of revisiting and reworking our hacking recommendations and intend to publish those recommendations soon.
B. Legislative Analysis
Reports of government hacking, and the legal regimes designed to permit it, continue to emerge from a number of different countries. In light of these reports, Privacy International has engaged in legislative analysis of government hacking powers in several countries.
In the Netherlands, Dutch Parliament is currently considering passage of the Draft Law on Intelligence and Security Services (“Draft Law”), which would govern the use and oversight of surveillance powers by the Dutch intelligence and security services. Although the power to hack is already contained in the Intelligence and Security Services Act 2002, which the Draft Law seeks to replace, the Draft Law purports to expand these powers. Privacy International advocated strongly against the hacking powers in the Draft Law, submitting comments on these and other powers during public consultation around the Draft Law.
In the UK, the Investigatory Powers Act (“IPA”) went into force in December 2016. The IPA is a new piece of framework legislation to govern the use and oversight of surveillance powers by British government authorities and places the power to hack on statutory footing for the first time. Privacy International advocated strongly against the hacking powers in the IPA, including through oral and written testimony to Parliament and as part of a broader coalition of organizations.[5]
We are currently in the process of analysing the law governing hacking powers in other countries and intend to continue publishing this work.
Footnotes:
[1] For further details, see our court submissions available here. The NSA and GCHQ have a long history of cooperation and work closely together in developing and deploying hacking capabilities. The NSA-GCHQ relationship must be viewed within the context of the Five Eyes alliance, an intelligence sharing arrangement between the US, UK, Australia, Canada and New Zealand. The roots of that alliance go back to 1946, when the US and the UK signed the UKUSA Agreement, a post-war signals intelligence sharing agreement. This agreement was later extended to encompass the other three members of the Five Eyes alliance.
[2] Chaos Computer Club (Germany), Greenhost (Netherlands), GreenNet (UK), Jinbonet (Korea), Mango Email Service (Zimbabwe), May First/People Link (US) and Riseup (US).
[3] Chaos Computer Club (Germany), GreenNet (UK), Jinbonet (Korea), May First/People Link (US) and Riseup (US).
[4] In our brief, we argued that what the FBI sought from Apple is hacking:
In neutral terms, hacking is about exploring — often in creative fashion — vulnerabilities in computer security. But it is only in its negative connotation that it encompasses the activity of exploiting these vulnerabilities to deliberately undermine security. That negative connotation of hacking is what the government seeks to compel from Apple. It asks Apple to design and then create software that purposefully creates cracks in the iPhone’s security.
[5] Privacy International, Written Evidence to the Joint Committee on the Draft Investigatory Powers Bill; Privacy International, Jan. 7, 2016; Caroline Wilson Palow, General Counsel, Privacy International, Oral Evidence to the Joint Committee on the Draft Investigatory Powers Bill, Dec. 9, 2015; Privacy International and Open Rights Group’s Submission to the Joint Committee on Human Rights on the Draft Investigatory Powers Bill, 7 Dec. 2015; Privacy International, Written Evidence to the Science and Technology Committee, 27 Nov. 2015.