Advanced Search
Content Type: Legal Case Files
Content Type: Press release
On 18th August 2025, Privacy International has issued a formal complaint to the UK Information Commissioner (ICO) about the Home Office’s (HO) use of two automated tools in immigration enforcement operations, which PI argues do not adequately comply with the UK General Data Protection Regulation (GDPR) and Data Protection Act 2018 (DPA 2018). The Identify and Prioritise Immigration Cases (IPIC) tool and the Electronic Monitoring Review Tool (EMRT) appear to be used to make life-altering…
Content Type: Long Read
On the basis of a year of legal research by PI as well as documents obtained by other civil society organisations, and evidence provided by legal representatives fighting these automated systems on behalf of their clients, on the 18th August 2025, we issued a formal complaint to the UK Information Commissioner (ICO) regarding the UK Home Office’s use of two ‘automated recommendation-making tools’ (ARMTs), the Identify and Prioritise Immigration Cases tool (IPIC) and the Electronic Monitoring…
Content Type: Advocacy
PI Opening Statement at PEGA Hearing on "Spyware used in third countries and implications for EU foreign relations"
Thank you very much for offering me the opportunity to give evidence before this Committee for another time on behalf of Privacy International (or PI) – a London-based non-profit that researches and advocates globally against government and corporate abuses of data and technology.
My opening statement will first briefly touch on the EU foreign policy’s priorities. I will…
Content Type: Press release
The decision by the EU’s oversight body follows a year-long inquiry prompted by complaints outlining how EU bodies and agencies are cooperating with governments around the world to increase their surveillance powers filed by Privacy International, Access Now, the Border Violence Monitoring Network, Homo Digitalis, International Federation for Human Rights (FIDH), and Sea-Watch.The complainants welcome the decision by the European Ombudsman and call on the Commission to urgently review its…
Content Type: Long Read
Introduction
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. Yet hacking presents unique and grave threats to our privacy and security. It is far more intrusive than any other surveillance technique, capable of accessing information sufficient to build a detailed profile of a person, as well as altering or deleting that information. At the same time, hacking not only undermines the security of targeted systems, but also has…
Content Type: Long Read
This piece was orignally published in Slate in February 2017
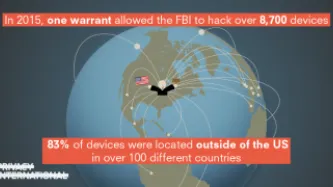
In 2015, the FBI obtained a warrant to hack the devices of every visitor to a child pornography website. On the basis of this single warrant, the FBI ultimately hacked more than 8,700 computers, resulting in a wave of federal prosecutions. The vast majority of these devices—over 83 percent—were located outside the United States, in more than 100 different countries. Now, we are in the midst of the first cases…
Content Type: Long Read
This piece originally appeared here.
On both sides of the Atlantic, we are witnessing the dramatic expansion of government hacking powers. In the United States, a proposed amendment to Rule 41 of the Federal Rules of Criminal Procedure would permit the government to obtain a warrant, in certain circumstances, to hack unspecified numbers of electronic devices anywhere in the world. Meanwhile, across the pond, the British Parliament is currently debating the Investigatory…