Uncovering Big Brother Inc
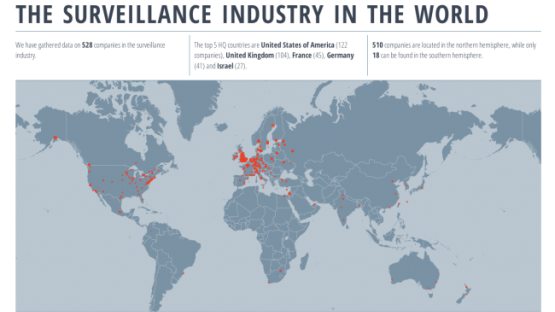
What happened
As we traveled the world we saw alarming use and spread of surveillance capabilities. From country to country we saw the same policy ideas, and the same kit. The role of industry to the growth of surveillance capability had never been exposed before.
What we did
In 1996 we published the first ‘Big Brother Incorporated’ study, identifying the vast numbers of technology firms who were investing in surveillance technologies. We were particularly surprised by the rise of German surveillance technology, not long after the fall of East Germany. That report led to increasing concerns about surveillance technology — by 2001 the European Parliament was investigating ‘technologies of political control’.
We continued to map the deals between industry and government, whether for ID cards or building ‘lawful intercept’ systems. We saw companies such as EDS across South East Asia in the 1990s, then Nokia Siemens in the late 2000s in Iran.
Following the ‘Arab Spring’, it was possible to identify which firms were selling what technologies to some oppressive regimes. By that time a whole new generation of firms and wares had arisen. We visited trade shows of the ‘Wiretapper’s Ball’, and tracked this industry. We worked with civil society organisations to index the firms and their wares — much of which is now available online at courtesy of Transparency Toolkit. Investigations by organisations like Citizen Lab exposed these companies for dealing with oppressive governments; as did some of our investigations as we mapped the firms, their capabilities and the people they affected in Central Asia, Colombia, Egypt, Ethiopia, Kenya, Morocco, Uganda and elsewhere. Hackers were able to expose two of the firms that sold hacking services and capabilities to governments.
Where things stand now
Large parts of the industry have been exposed. Some divested in some capabilities. Some fell apart. But there is still a vibrant industry selling its wares across the world.
Export control regulations have affected their abilities to sell and have forced governments to reveal information about where they are selling -- allowing the public, journalists and others to hold these companies and governments accountable.
What we learned
Exposing firms is not enough. Exposing capabilities is not enough either. Stopping the flow of technology is essential, both through stopping their purchasing and deployment, but also by preventing their export.
Hard lessons
Seeking regulatory solutions must be done with great care so as to not have serious side-effects. We believed that regulating tools that enabled government hacking could be done through export controls. We were slow to listen when experts raised concerns about how restraints on the free flow of research would damage security research, and in turn, security.
What we are doing now
We are looking to see how and why countries around the world - including authoritarian regimes - are procuring these technologies and capabilities in the first place. Too often they are provided with the means incentives and resources by some of the world’s richest governments, including China, the EU, Russia, the US, and the UK. We are exposing these arrangements and seeking reform.
Verint Israel utility room © Mari Bastashevski in Private Interests: Monitoring Central Asia.