Phone Monitoring
Phone networks are divided between two networks: the physical and the mobile. The physical runs on the Public Switched Telephone Network (PSTN) that serves your home phone. Mobile networks are dominant in the age of communication and are used to relay mobile communications to the PSTN. The most prominent mobile networks are GSM networks (Global System for Mobile communications) and are what we use everyday to communicate with one another. Another system is known as CDMA (Code Division Multiple Access) that operates in a similar way and exists mainly in North America. Additionally, there are Next Generation Networks (NGN), which broadly consist of the more well known terms of 3G and 4G. These networks turn your mobile device into a data transmitter that smartphones use to deliver applications on the go. These networks are our global system of communications. They are also the target of multiple surveillance technologies.
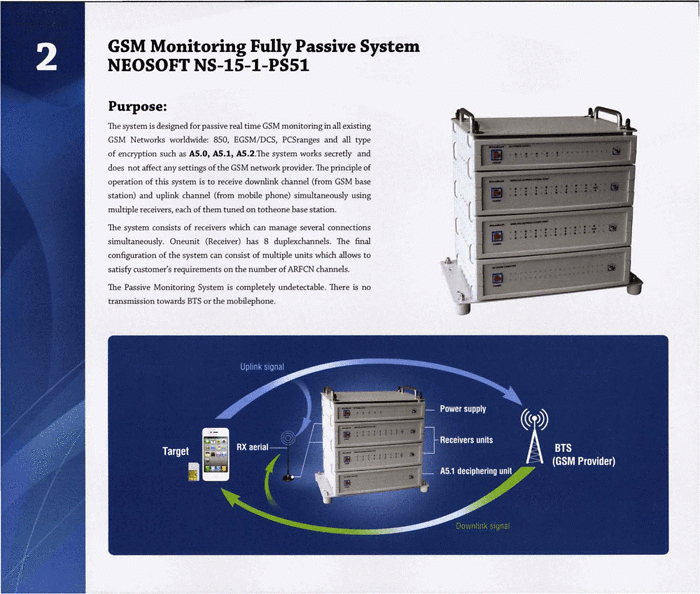
As mobile phone data travels over the GSM network, it may be passively intercepted between the phone and the base station it is communicating with. The base station is the phone's first point of contact to the rest of the mobile phone network. Passive interception operates by tuning into the base station and receiving the uplink signal from the mobile phone and the downlink signal from the base station. The uplink signal is the information being sent from the phone to the base station: the content of the call and of the message. The downlink signal is the information being sent from the base station to the phone: replies to the phone call and messages.
By simply tuning the equipment’s own receiver onto the correct frequencies that the uplink and downlink signals operate on phone monitoring technology can gain access to the information being transmitted over the network between the phone and the base station. The additional protections provided by GSM networks come in the form of ciphers A.5/1 A.5/2, which are designed to protect the privacy of the communication. Both of these ciphers had been reverse engineered by 1999, which means they were completely decipherable and that in practice all communications sent across the GSM network are prone to interception, deciphering and storage within a matter of seconds. A.5/2 is in fact prohibited from being used by mobile phones and has been since 2006 because of the concerns around its weakness. Many of the surveillance technologies sold in the market offer real time A.5/1 and A.5/2 deciphering features.
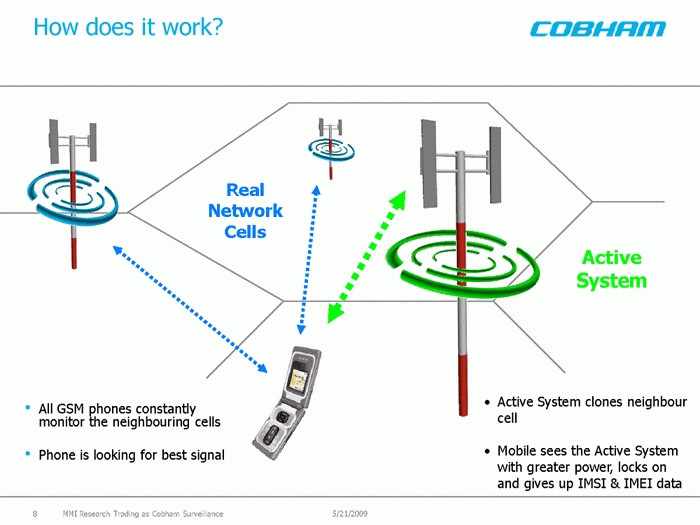
An IMSI Catcher is a phone monitoring kit that provides active intercept capabilities. Traditionally, IMSI Catchers (or Stingrays as they are known in the United States of America) can capture a number of different pieces of identifiable information including the IMEI and the IMSI: identifiers for your phone and SIM Card respectively. Nowadays IMSI Catchers can record voice and message data as they travel through mobile networks.
An IMSI Catcher performs interception by presenting itself as a base station amongst the mobile network: the station that your phone connects to when it wants to place a call or send a message. The IMSI Catcher acting as a base station then enters the network as the most powerful base station available, meaning that all mobile phones operating within the same area connect to the IMSI Catcher's base station. Once connected to the IMSI Catcher’s base station the Catcher has the mobile phone provide to it its IMSI and IMEI data. Once these details have been gathered it becomes possible to monitor the operation of the phone: the voice calls taking place, the messages being sent and the location of the phone.
The system is described as active because of its focus in enticing the signal towards it, rather than passive monitoring which does not entice the signal but sits silently between the phone and the base station and does not replace the base station operation like an IMSI Catcher. The benefit of passive interception is that it is almost impossible to detect its operation, whereas an IMSI Catcher could be detected by a network operator because of the active enticing that it performs.
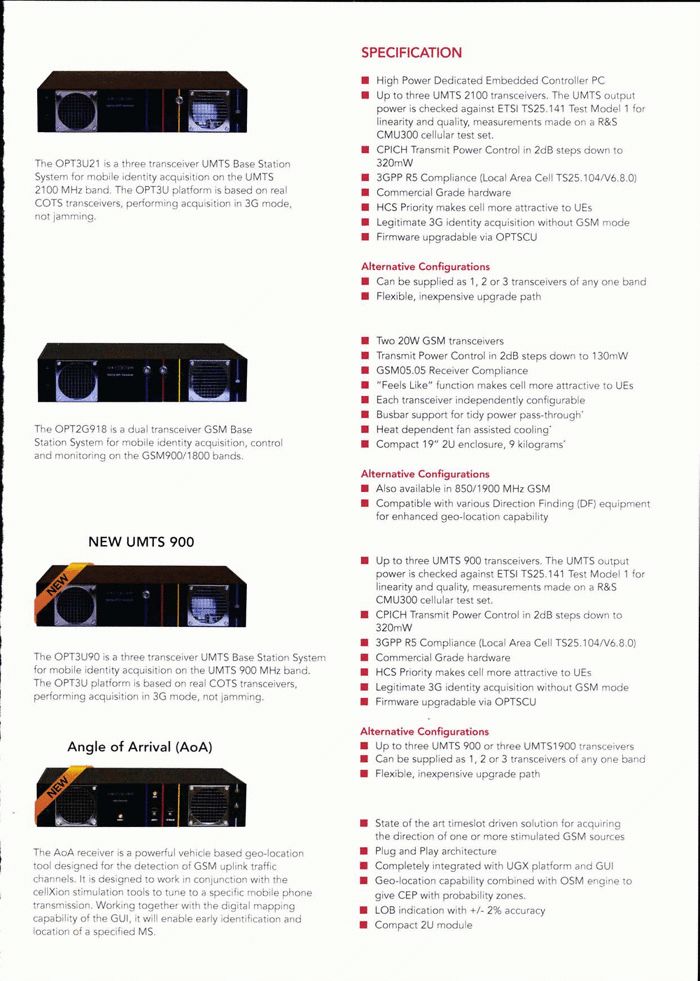
There are many networks now in operation across mobile networks all with different capabilities, features and operating standards, which means that phone monitoring technology needs to adapt to interception on these new networks also. 3G networks, referred to as UMTS, are different from 2G networks, which are better known as GSM/CDMA.
Phone monitoring on 3G networks can identify handsets (grabbing the IMSI and the IMEI), and depending on decryption capabilities intercept messages or content. 3G jammers are now being introduced into phone monitoring systems: identifying the phones operating on 3G (UMTS) then forcing them into 2G (GSM) mode for interception of content using technologies that can rapidly decrypt A5.0/A5.1/A5.2 and thus open up the phone's activities for interception over the air.
Location tracking of phones in 3G can be achieved without forcing the phone onto 2G. This signals an increasing ability to operate monitoring on 3G networks, meaning that it will be shown that interception over 3G networks of call content and messages is not far away.
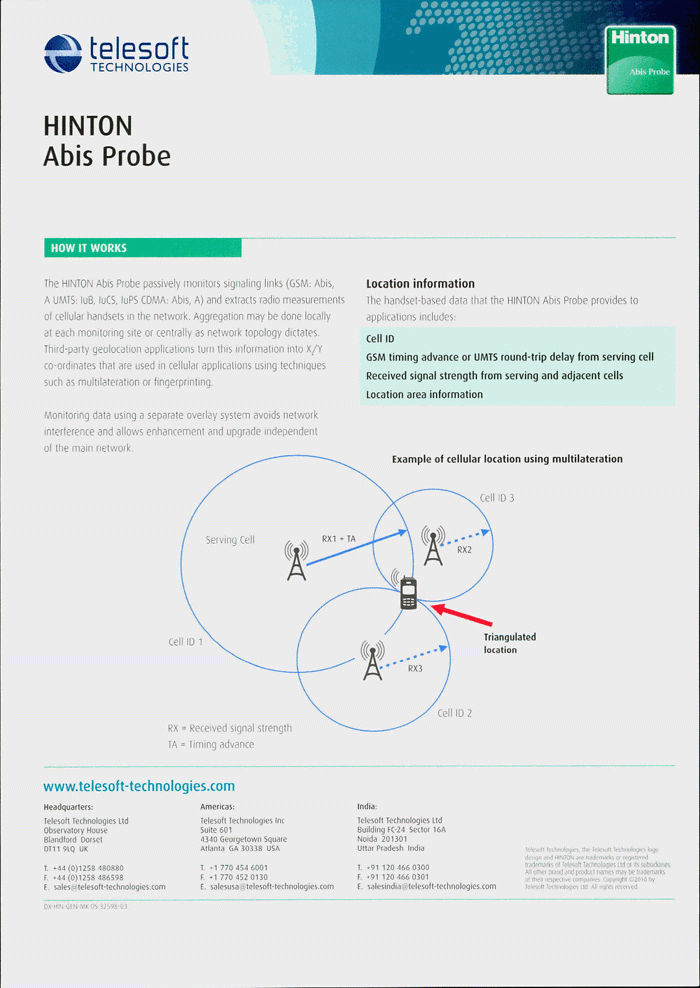
Tracking is able to occur through triangulation of the phone to the nearest cell tower also. Phones are always communicating with multiple base stations, searching for the strongest signal that will best host a call or send a message. It is this constant searching for powerful connections that makes IMSI Catchers so effective. It is also why location tracking is able to provide accurate readings, sometimes within 30 metres of a target’s actual location.
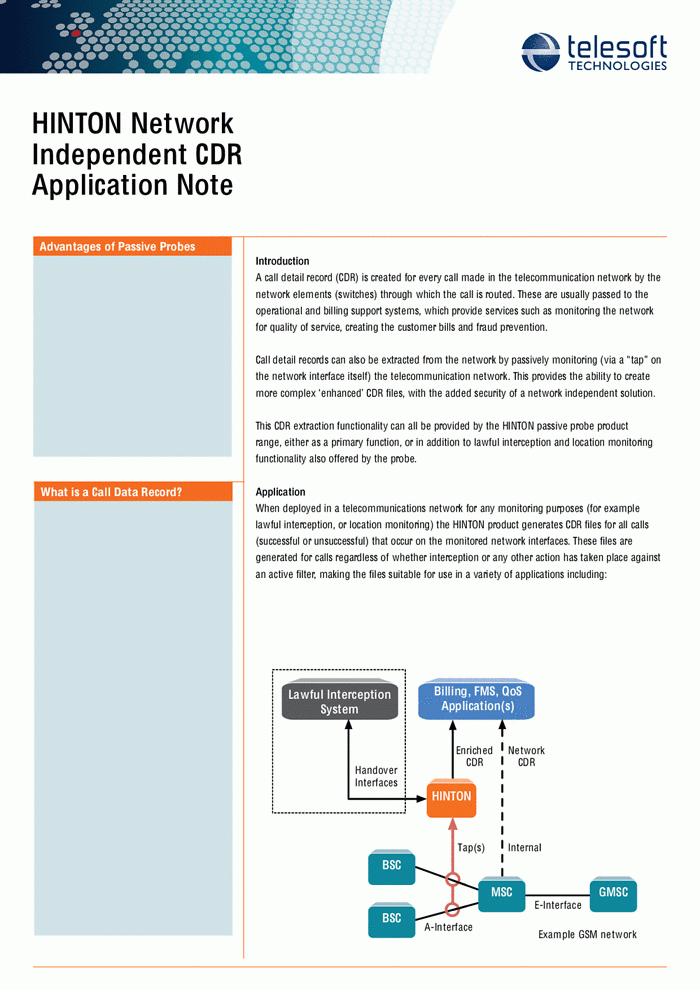
It must be remembered that Off-the-Air interception is not the only form of interception from mobile phones. Access can also be achieved through physical probes placed on mobile networks. This involves moving further into the mobile network, past the wireless base stations and into the Mobile Switching Centres that operate and host information on groups of base stations. The information that can be collected in addition to call content is referred to as Call Data Records (CDR), the metadata of telephone calls which- as with metadata gathered via internet monitoring- holds much information that allows for the identification and tracking of targets.
These probes operate in what is referred to as a lawful interception framework. This does not mean that the interception is guaranteed to be lawful just that it meets technical standards set by a body known as ETSI (European Technical Standards Institute) that requires information to be handed over by service providers in a certain format with certain pieces of information attached. The interception of that information can still be fundamentally illegal, unjustifiably violating a person’s privacy.