Search
Content type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content type: News & Analysis
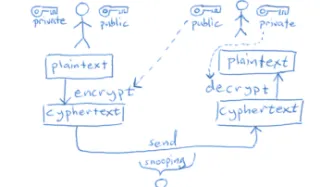
We found the above image here.
Background
Email is hard to secure. For years we've been trying to build security on top of email, such as through technologies like Pretty Good Privacy (PGP) and the open source implementation: GnuPG (GPG).
What happened
In the past 48 hours, there have been very scary looking reports recommending people switch off PGP in their email clients.
The TL;DR version of this post is:
PGP is not broken by this attack
You absolutely should not stop…
Content type: Impact Case Study
What is the problem
Business models of lots of companies is based on data exploitation. Big Tech companies such Google, Amazon, Facebook; data brokers; online services; apps and many others collect, use and share huge amounts of data about us, frequently without our explicit consent of knowledge. Using implicit attributes of low-cost devices, their ‘free’ services or apps and other sources, they create unmatched tracking and targeting capabilities which are being used against us.
Why it is…
Content type: Impact Case Study
What happenedGovernments continuously seek to expand their communications surveillance powers. In the 1990s it was in the context of applying telephone surveillance laws to the internet. In the 2000s a spate of new laws arrived in response to 9/11. Expansions were then sought to monitor over-the-top services within the framing of Web 2.0. Then in the post-Snowden environment Governments rushed to legislate their previously secret powers.What we didWe supported…
Content type: News & Analysis
Dear Politicians,
With elections coming up and quite a few cringe-worthy comments that have come from many of you and from all sides of the political spectrum, we figured it was time to have a chat about encryption.
First, let’s say what you shouldn’t do:
call for boycotts of companies because they protect their users’ data even from the companies themselves.
say something like “we’ll develop a Manhattan-level project on this” (which, as we’ll remind you, ended up with the creation of a…
Content type: Advocacy
Privacy International's submission on the right to privacy in Thailand, Human Rights Committee, 119th Session.
In our assessment to the Committee, national legislation governing surveillance is inadequate, unclear as to the powers, scope and capacity of state surveillance activities and thus it falls short of the required human rights standards to safeguard individuals from unlawful interference to the right to privacy.
Content type: News & Analysis
Technologists hoped the “Crypto Wars” of the 1990s – which ended with cryptographers gaining the right to legally develop strong encryption that governments could not break – was behind them once and for all. Encryption is a fundamental part of our modern life, heavily relied on by everything from online banking and online shopping services to the security our energy infrastructure.
However, from comments by the French and German governments about creating a European initiative to circumvent…
Content type: Report
The explosion of telecommunications services has improved the ability for human rights groups to disseminate information worldwide. New telephone, facsimile and computer communications have created opportunities for human rights groups to improve organizing and to promote human rights faster and at a lower cost than ever before. However, these new technologies can be monitored by governments and other groups seeking to monitor the activities of human rights advocates. For this reason, human…