How intrusive is communications data?
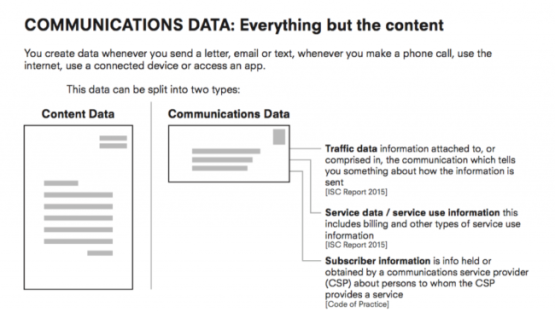
It is common ground that bulk collection of content would be a deprivation of the right to privacy. That is an inexcusable or unjustifiable step too far. Repeatedly the Government whether in litigation or legislating, has emphasised that they are not taking content in bulk. Content is the forbidden ground.
This has resulted in the Government seeking to explain, for example, what parts of an email would constitute content and meta data. Within the Investigatory Powers Act it has led to the creation a plethora of definitions and types of communications data, narrowing what falls within the definition of ‘content’ and thus increasing the volume of data which can be subject to data retention and access powers.
However, that communications data can reveal private information on individuals as much as content data has been long recognised by Courts and expert bodies.
The essence of the truth grappled with by the European Court of Justice in the Tele2/Watson case regarding communications data retention, is that this somewhat old-fashioned distinction between content and communications data or traffic data is, in fact, no longer fit for purpose as some kind of formalistic distinction. The European Court of Justice say, entirely realistically, entirely accurately, that communications data, when collected in aggregate about one or a number of individuals is potentially no less sensitive, in their words, than the actual content.
The boundary between content and communications, which may have worked pre-internet, in a world of intermittent phone calls and letters sent by post or telegram, simply becomes unworkable or unsafe in an age of 24-hour browsing, mailing, messages, instant apps, where that replaces conventional social interaction. When people live their lives online, where their smart phone is a tracking device of their every movement, the boundary is simply unsafe because of the welter of information derivable from communications data. It tells you everything, or nearly as much as the content itself.
Communications data includes, but is not limited to, visited websites, email contacts, to whom, where and when an email is sent, map searches, GPS location and information about every device connected to every wifi network in the United Kingdom, which includes Smart Tech, such as Nest, iKettle, Smart Barbie, Amazon Echo and others.
In the UK, we have one of the highest rates of internet shopping in the world. We have one of the highest rates of penetration of smart phones in the world. We take our TV and our entertainment from internet services like Netflix, Apple TV, Amazon Prime, You Tube, all of which is traceable and trackable via communications data.
A visit to an IP address, hosting a medical self-diagnosis website, followed by a visit to your GP’s website, followed by a telephone call to an oncologist, followed by an appointment with a private client solicitor and then a hospice may well reveal that the person in question has terminal cancer.
Patterns of call behaviour to particular competitors, lawyers and then bankers and then accountants might be entirely dispositive in showing that a takeover is in prospect in relation to a particular company.
Communications data, is massively valuable. It is massively valuable in the hands of the state, but it also liable to misuse and a valuable target for theft, because one can see very readily how the blackmailer or the commercially unscrupulous, if they can use or get their hands upon such material, may use it in an ulterior way.
Further, the 21st century has brought with it rapid development in the technological capabilities of Governments to acquire, extract, filter, store, analyse and disseminate the communications of whole populations. The means of analysing the information have improved exponentially due to developments in automated machine learning and algorithmic designs.
As stated in Tele2 Sverige AB v. Post- Och telestyrelsen (C-203/15); Secretary of State for the Home Department v. Tom Watson et. al. (C-698/16), Joined Cases, Court of Justice of the European Union, Grand Chamber, Judgment (21 December 2016):
99. That data, taken as a whole, is liable to allow very precise conclusions to be drawn concerning the private lives of the persons whose data has been retained, such as everyday habits, permanent or temporary places of residence, daily or other movements, the activities carried out, the social relationships of those persons and the social environments frequented by them. In particular, that data provides the means... of establishing a profile of the individuals concerned, information that is no less sensitive, having regard to the right to privacy, than the actual content of communications.
The UNHCRC has stressed[1] that the distinction between the seriousness of interception of metadata and content is “not persuasive” and “any capture of communications data is potentially an interference with privacy [...] whether or not those data are subsequently consulted or used.” The mere fact of such capture may indeed have a “potentially chilling effect on rights, including those to free expression and association”. The Commissioner concluded that “[m]andatory third-party data retention [...] appears neither necessary not proportionate (paragraph [26] at p.9).[2]
The UN Human Rights Council noted, in a resolution adopted by consensus, “certain types of metadata, when aggregated, can reveal personal information that can be no less sensitive than the actual content of communications and can give an insight into an individual’s behaviour, social relationships, private preferences and identity” (A/HRC/RES/34/7).
Further, as the Council of Europe’s Commissioner has noted, “extensive research has failed to show any significant positive effect on clear-up rates for crime, and especially not for terrorism-related crime, as a result of compulsory data retention.”[3] As he stressed, metadata can be “unreliable and can unwittingly lead to discrimination on grounds or race, gender, religion or nationality. These profiles are constituted in such complex ways that the decisions based on them can be effectively unchallengeable: even those implementing the decisions do not fully comprehend the underlying reasoning”[4].
Footnotes
[1] In its report published on 30 June 2014, “The right to privacy in the digital age” (A/HRC/37), see fn.6.
[2] See also the report of the UN Special Rapporteur on the promotion and protection of human rights and fundamental freedoms while countering terrorism, Ben Emmerson QC, UN doc. (A/69/397) at [55] (Annex 7).
[4] https://rm.coe.int/16806da51c page 113
[5] https://rm.coe.int/16806da51c page 8