Search
Content type: Report
Privacy International’s submissions for the Independent Chief Inspector of Borders and Immigration inspection of the Home Office Satellite Tracking Service Programme
The Home Office have introduced 24/7 electronic monitoring and collection of the location data of migrants via GPS ankle tags. This seismic change cannot be overstated. The use of GPS tags and intention to use location data, kept for six years after the tag is removed, in immigration decision-making goes far beyond the mere…
Content type: News & Analysis
As Amnesty International and Forbidden Stories continue to publish crucial information about the potential targets of NSO Group’s spyware, we know this much already: something needs to be done.
But what exactly needs to be done is less obvious. Even though this is not the first time that the world has learned about major abuses by the surveillance industry (indeed, it’s not even the first time this month), it’s difficult to know what needs to change.
So how can the proliferation and use of…
Content type: Explainer
An array of digital technologies are being deployed in the context of border enforcement. Satellite and aerial surveillance are part of the surveillance toolkit and yet, they are also used by organisations seeking to hold government actions to account and improve efficacy of their own work. To effectively critique state use and delve into potential benefits of satellite and aerial surveillance, we must first understand it.
In this explainer we dig into a technology which many are aware of for…
Content type: Long Read
The Grand Chamber of the European Court of Human Rights ruled that the UK government’s historical mass interception program violates the rights to privacy and freedom of expression. The Court held that the program “did not contain sufficient “end-to-end” safeguards to provide adequate and effective guarantees against arbitrariness and the risk of abuse.” As a result the Court ruled that UK law "did not meet the “quality of law” requirement and was therefore incapable of keeping the “…
Content type: News & Analysis
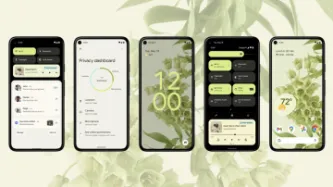
On May 18th 2021 Google held its annual developer conference, Google I/O, where the company announces a number of innovations, products and software updates that will hit the market in the months to come. Among these announcements, the company introduced Android 12, its latest mobile Operating System (OS), that came with headline grabbing privacy features.
Possibly trying to catch up with Apple, which is positioning itself as a privacy-friendly tech company and gave the adtech industry a kick…
Content type: Long Read
What’s the ruling all about?The Constitutional Court of South Africa in a historic judgment declared that bulk interception by the South African National Communications Centre is unlawful and invalid. Furthermore, the Constitutional Court found that the Regulation of Interception of Communications and Provision of Communication-Related Information Act (RICA) 1) was deficient in failing to provide at least a post-notification procedure for subjects of interception; 2) failed to ensure the…
Content type: Video
Find out more on our website: https://privacyinternational.org/long-read/4206/qa-eus-top-court-rules-uk-french-and-belgian-mass-surveillance-regimes-must-respect
And make sure we can keep taking these fights to court: support.privacyinternational.org
You can listen and subscribe to the podcast where ever you normally find your podcasts:
Spotify
Apple podcasts
Google podcasts
Castbox
Overcast
Pocket Casts
Peertube
Youtube
Stitcher
And more...
Content type: News & Analysis
On September 16, Google announced their intention to enforce a new "stalkerware" policy after a 15 day grace period ending on 1 October 2020.The policy change states that the Google Play Store will only host stalkerware apps that give "a persistent notification is displayed while the data is being transmitted."
In its announcement, Google defines stalkerware as "Code that transmits personal information off the device without adequate notice or consent and doesn't display a persistent…
Content type: News & Analysis
An estimated 90% of the world’s student population are affected by school closures in the Covid-19 pandemic. And, in the absence of physical space, education technology companies are stepping in to fill the gap. There are plenty of reasons to be excited about the potential of technology to provide support, but it’s important to consider the ongoing implications of which technology we choose, and the implications for those families who don’t have access to them in the first place.That’s why we’…
Content type: News & Analysis
A few weeks ago, its name would probably have been unknown to you. Amidst the covid-19 crisis and the lockdown it caused, Zoom has suddenly become the go-to tool for video chat and conference calling, whether it’s a business meeting, a drink with friends, or a much needed moment with your family. This intense rise in use has been financially good to the company, but it also came with a hefty toll on its image and serious scrutiny on its privacy and security practices.
While Zoom already had a…
Content type: Examples
On the second day of India's nationwide shutdown due to the COVID-19 outbreak, the Karnataka government published the home addresses of quarantined residents, as a deterrent to breaking the rules. The list included individuals who had flown in from a foreign country and been asked to stay indoors for two weeks but who had not tested positive for the novel coronavirus. Although the government deleted a tweet announcing its intention, the list is still available on its website and is circulating…
Content type: Case Study
The right to privacy is crucial to protect a couple’s equal rights within marriage.
The recent rise of spyware as an “off-the-shelf” product that anyone can purchase has been extremely worrying, as installing spyware on someone else’s phone means getting access to their contacts, their messages, their google searches, their location and more - all without them knowing.
Spyware is, increasingly, becoming another way for abusive spouses to control and monitor their partners. Nearly a third of…
Content type: Impact Case Study
What HappenedOn 5 June 2013, The Guardian published the first in a series of documents disclosed by Edward Snowden, a whistleblower who had worked with the NSA. The documents revealed wide-ranging mass surveillance programs conducted by the USA’s National Security Agency (NSA) and the UK’s Government Communications Headquarters (GCHQ), which capture the communications and data of hundreds of millions of people around the world. In addition to revealing the mass surveillance programs of the NSA…
Content type: Examples
In 2013, Edward Snowden, working under contract to the US National Security Agency for the consultancy Booz Allen Hamilton, copied and leaked thousands of classified documents that revealed the inner workings of dozens of previously unknown surveillance programs. One of these was PRISM, launched in 2007, which let NSA use direct access to the systems of numerous giant US technology companies to carry out targeted surveillance of the companies' non-US users and Americans with foreign contacts by…
Content type: News & Analysis
In our latest report “Who’s that knocking at my door? Understanding surveillance in Thailand”, we highlighted various methods of surveillance that the Thai Government employs. Included in these methods was the finding that Microsoft was the only technology company which by default trusts the Thai Government’s root certificate. Root certificates ensure the validity of a website, and protect users from being tricked into visiting a fake, insecure website. Most technology companies including Apple…
Content type: Long Read
In July 2015, representatives of a private company met in a parking lot in Pretoria, South Africa to sell phone tapping technology to an interested private buyer. What they did not know was that this buyer was a police officer. The police had been tipped off that the company was looking to offload the surveillance technology, an IMSI catcher, to anyone who would buy it. It is illegal to operate such surveillance technology as a private citizen in South Africa, and illegal to buy…
Content type: Long Read
This piece was written by Ashley Gorski, who is an attorney at the American Civil Liberties Union, and PI legal officer Scarlet Kim and originally appeared in The Guardian here.
In recent weeks, the Hollywood film about Edward Snowden and the movement to pardon the NSA whistleblower have renewed worldwide attention on the scope and substance of government surveillance programs. In the United States, however, the debate has often been a narrow one, focused on the…
Content type: Long Read
This week, Privacy International, together with nine other international human rights NGOs, filed submissions with the European Court of Human Rights. Our case challenges the UK government’s bulk interception of internet traffic transiting fiber optic cables landing in the UK and its access to information similarly intercepted in bulk by the US government, which were revealed by the Snowden disclosures. To accompany our filing, we have produced two infographics to illustrate the…
Content type: News & Analysis
Thank you to those of you who joined our campaign, 'Did GCHQ Illegally Spy on You?'. If you made a claim to the Investigatory Powers Tribunal (IPT) - the court that hears claims about surveillance by public bodies, including the intelligence agencies - to find out if GCHQ has illegally obtained your communications, you will have probably received a letter or email from the IPT by now. We've written a 'Frequently Asked Questions' (FAQ) to help clarify what the ruling means and how you can now…
Content type: Long Read
Written by: Centre for Internet and Society
This guest piece was written by representatives of the Centre for Internet and Society (CIS). It does not necessarily reflect the views or position of Privacy International.
Introduction
As part of the State of the Surveillance project, CIS conducted a review of surveillance law, policy, projects, and trends in India. Below we provide a snap shot of key legal provisions governing surveillance in India and touch on…
Content type: Press release
Today’s report by the Joint Committee on the Investigatory Powers Bill is the third committee report that concludes that the Home Office has failed to provide a coherent surveillance framework.
The Joint Committee on the Investigatory Powers Bill today published a 198 page report following a short consultation period between November and January. Their key findings are that:
- the definitions in the bill need much work, including a meaningful and comprehensible…
Content type: News & Analysis
Internet Connection Records are a new form of communications data created by the Investigatory Powers Bill at Parts 3 and 4. They constitute an unlawful interference with privacy with the ability to provide a highly detailed record of the activities of individuals, profiling their internet habits.
Clause 62 of the Investigatory Powers Bill (“IP Bill”) permits a wide range of public authorities to collect Internet Connection Records, however throughout debates on this highly controversial new…
Content type: Long Read
Written by Eva Blum-Dumontet
A recent case of lèse-majesté in Thailand (speaking ill of the monarchy) is a worrying example of how Western companies do not just work with governments that fall short of international human rights standards, but can actually facilitate abuses of human rights.
Our investigation on the trial of Katha Pachachirayapong — accused of spreading rumours on the ill-health of the King Bhumibol Adulyadej, thereby causing sharp falls in the Thai stock market — reveal the…
Content type: News & Analysis
According to Snowden documents analysed by Privacy International, the Australian Signals Directorate had access to and used PRISM, a secret US National Security Agency program which provides access to user data held by Google, Facebook and Microsoft.
This is the third spy agency of the 'Five Eyes' alliance confirmed to have had secret access to Silicon Valley company data - an alliance whose rules and policies remain classified. Earlier this year, a British court ruled that GCHQ access to…
Content type: News & Analysis
Lebanon was part of the drafting committee for the Universal Declaration of Human Rights, and by co-sponsoring both UN General Assembly resolutions on the right to privacy in the digital age (December 2013 and December 2014), Lebanon has recently reaffirmed its commitment to its obligations to uphold the right to privacy.
And yet, Lebanon's progressive positions on the right to privacy at the UN could not be further away from the situation in the country itself.
Once seen as…
Content type: Press release
British intelligence services acted unlawfully in accessing millions of people’s personal communications collected by the NSA, the Investigatory Powers Tribunal ruled today. The decision marks the first time that the Tribunal, the only UK court empowered to oversee GHCQ, MI5 and MI6, has ever ruled against the intelligence and security services in its 15 year history.
The Tribunal declared that intelligence sharing between the United States and the…
Content type: News & Analysis
Going into 2014, there were high hopes for advancing privacy protections and to finally have the debate around surveillance we've been clamouring for. Privacy was even Dictionary.com's word of the year in 2013. Europe was on the edge of passing new strong privacy laws, despite protests from industry and governments. Parliaments in Canada and the United Kingdom had pushed back against expanding surveillance laws. Transparency reports were beginning to shine a more comprehensive picture on…
Content type: News & Analysis
We have learnt a lot in the last year about the dirty games GCHQ and NSA are playing to infiltrate the networks, tools and technologies we all use to communicate. This includes forcing companies to handover their customers’ data under secret orders, and secretly tapping fibre optic cablesbetween the same companies’ data centers.
Not content with that, we know now GCHQ are targeting companies systems administrators, exploiting the routers and switches in their networks to…
Content type: News & Analysis
A strong, unified voice from the tech industry is absolutely essential to reforming the mass and intrusive surveillance programs being run by the Five Eyes, so we welcome today's statement from AOL, Apple, Google, Facebook, LinkedIn, Microsoft, Twitter, and Yahoo.
Companies have obligations to respect human rights and not be complicit in mass surveillance. Given what has been publicly revealed over the past six months, we must know for certain that the companies we entrust with our information…
Content type: Long Read
Privacy International filed formal complaints with the Organisation for Economic Cooperation and Development (OECD) in the UK against some of the world’s leading telecommunication companies, for providing assistance to British spy agency GCHQ in the mass interception of internet and telephone traffic passing through undersea fibre optic cables.
According to recent reports, BT, Verizon Enterprise, Vodafone Cable, Viatel, Level 3, and Interoute granted access to their fibre optic…