Advanced Search
Content Type: Examples
In the run-up to the May 2019 European Parliament elections, Google announced it would launch a new set of transparency tools to combat voter manipulation. Before being allowed to buy advertising on Google platforms, campaigns will be required to verify their identity, and approved ads will be required to display the identity of their purchaser. Google will build a real-time searchable database of all political ads and show their purchasers, costs, and demographics. Facebook announced similar…
Content Type: Examples
A 2018 study found that Twitter bots played a disproportionate role in spreading the false claim, made by US President Donald Trump shortly after winning the election but losing the popular vote in November 2016, that 3 million illegal immigrants had voted for Democratic opponent Hillary Clinton. After examining 14 million messages shared on Twitter between May 2016 and May 2017, Indiana University researchers found that just 6% of Twitter accounts identified as bots spread 31% of "low-…
Content Type: Examples
Facebook's latest tool for inspecting political ads showed that in the run-up to the US mid-term elections in November 2018, many of the same politicians who had been questioning Facebook about privacy and leaked user data were spending campaign funds on advertisements on the service. Between 2014 and 2018, the digital percentage of political spending rose from 1% to 22% (or about $1.9 billion); between May and November 2018 political spending on Facebook and its subsidiaries came to nearly $…
Content Type: Examples
In November 2018, the UK government announced that 11 local authorities across England would participate in Voter ID pilots in the interest of gaining "further insight into how best to ensure the security of the voting process and reduce the risk of voter fraud". Five local authorities participated in pilots in the 2017 general election. The new pilots will test four models of identification checks: photo ID (Pendle, East Staffordshire, Woking), photo and non-photo ID (Ribble Valley, Broxtowe,…
Content Type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content Type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content Type: Long Read
The UK border authority is using money ring-fenced for aid to train, finance, and provide equipment to foreign border control agencies in a bid to “export the border” to countries around the world.
Under the UK Border Force’s “Project Hunter”, the agency works with foreign security authorities to bolster their “border intelligence and targeting” capabilities with UK know-how and equipment.
As well as the provision of equipment and training, the Border Force is also advising countries on…
Content Type: Advocacy
Cases of female and gender diverse public figures being targeted with online harassment have become sadly common in the news. Female politicians are particularly affected – although journalists and in particular sports commentators are also frequently targeted as well. In some cases, the harassment goes as far death and rape threat for women and gender diverse people who dare speaking publicly. Beyond the freedom of speech implications – as we risk seeing women and gender diverse people being…
Content Type: News & Analysis
PI has today written to Google, Instagram, Snapchat, TicTok, Twitter, YouTube, and WhatsApp to ask for more information about their steps to tell people why they are seeing ads. Facebook recently announced expanding the company's ad transparency measures to include more information about why an ad or content appears in a user's newsfeed. While Facebook has a lot more to do, it is important that all technology companies provide advertising transparency.
Recently, we have seen how platforms…
Content Type: Long Read
Cellebrite, a surveillance firm marketing itself as the “global leader in digital intelligence”, is marketing its digital extraction devices at a new target: authorities interrogating people seeking asylum.
Israel-based Cellebrite, a subsidiary of Japan’s Sun Corporation, markets forensic tools which empower authorities to bypass passwords on digital devices, allowing them to download, analyse, and visualise data.
Its products are in wide use across the world: a 2019 marketing…
Content Type: Explainer graphic
You can also read a more detailed explainer about police hacking here.
Content Type: News & Analysis
The Committee on Foreign Investment in the United States (CFIUS) is trying to force the Chinese owner of the gay dating app Grindr to sell the app because of national security concerns. This is the first time the committee has considered the national security implications of a foreign social media app.
Early last year, the Chinese company Beijing Kunlun Tech purchased the Californian-based dating app. Kulun had already owned 60 per cent of Grindr since 2016. Yet, it is only now – with an…
Content Type: News & Analysis
Today, the Kenyan Government is starting their biometric registration exercise known as NIIMS, leading to the issuing of Huduma Namba ID numbers. Along with our colleagues and partners in the human rights community in Kenya, we are very worried about the ramifications of this system for people in Kenya, and particularly for marginalised communities.
Thanks to the hard work and timely action of civil society in Kenya, the judiciary has intervened at the last minute. A court ruling on…
Content Type: News & Analysis
This past weekend, in an Op-Ed in the Washington Post, Mark Zuckerberg called for new regulations to address harmful content, electoral integrity, privacy and data portability.
Nine years since he proclaimed that privacy is no longer a social norm, four years since Facebook noticed broadscale harvesting and exploitation of their users' data by third party companies and chose not to tell us about it, two years since he denied there were any abuses of data in political campaigns, and…
Content Type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content Type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
Content Type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content Type: Advocacy
Privacy International's submission to the Human Rights Committee on a future General Comment on Article 21 of the International Covenant on Civil and Political Rights (ICCPR).
In this submission, Privacy International aims to provide the Committee with information on how surveillance technologies are affecting the right to peaceful assembly in new and often unregulated ways.
Based on Privacy International’s research, we provide the following observations:
the relationship between right…
Content Type: State of Privacy
Introduction
Acknowledgment
The State of Surveillance in Tunisia is the result of an ongoing collaboration by Privacy International and partners.
On 14 February 2023, the United Nations High Commissioner for Human Rights voiced concern over the deepening crackdown in Tunisia targeting perceived political opponents of President Kais Saied as well as civil society.
We have updated this page to reflect important changes in the state of surveillance in Tunisia.
Key privacy facts
1.…
Content Type: News & Analysis
We found this image here.
Today, a panel of competition experts, headed by Professor Jason Furman, the former chief economic adviser of in the Obama administration, confirmed that tech giants, like Facebook, Amazon, Google, Apple and Microsoft, do not face enough competition.
Significantly, the report finds that control over personal data by tech giants is one of the main causes preventing competition and ultimately innovation.
Privacy International's research has shown clear examples of…
Content Type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
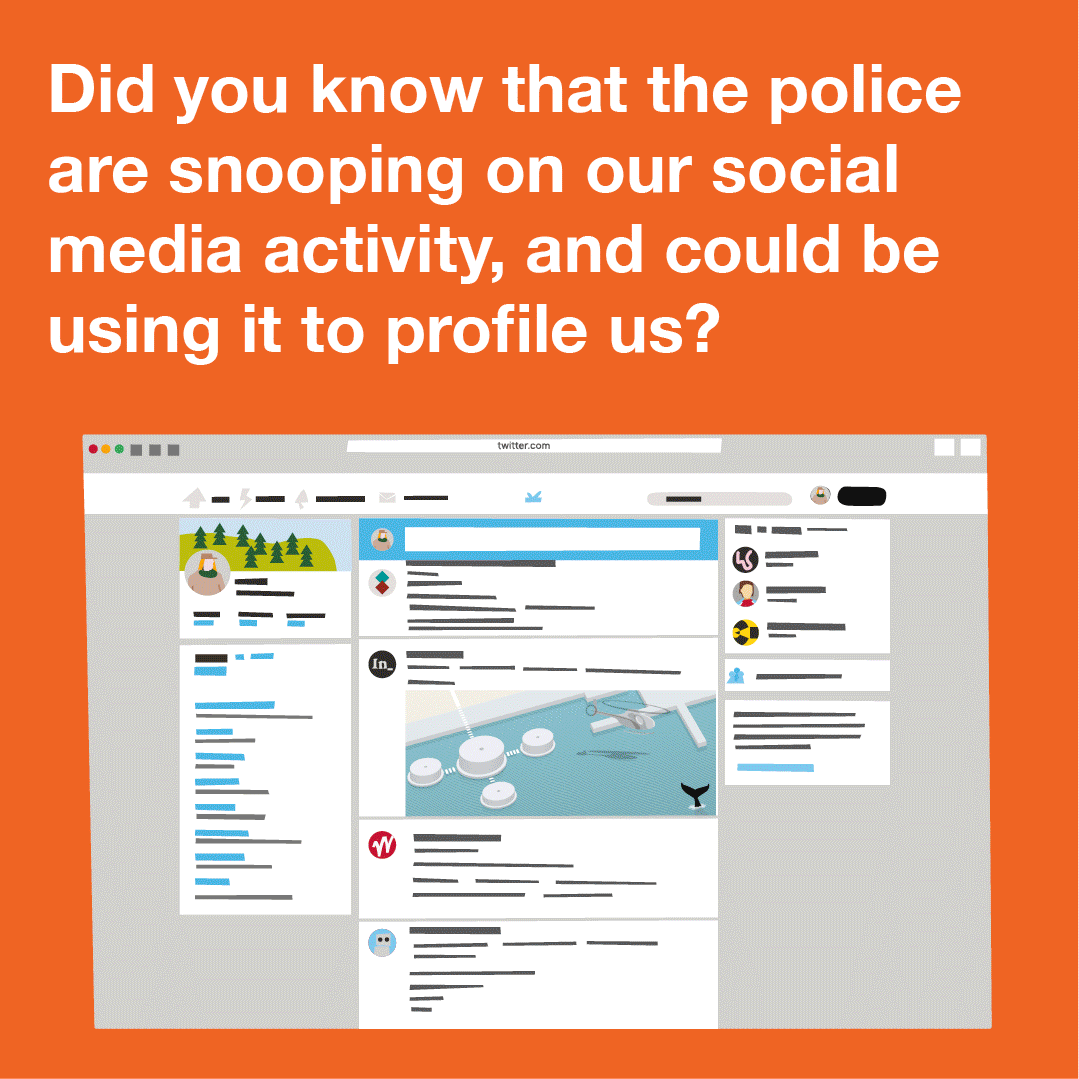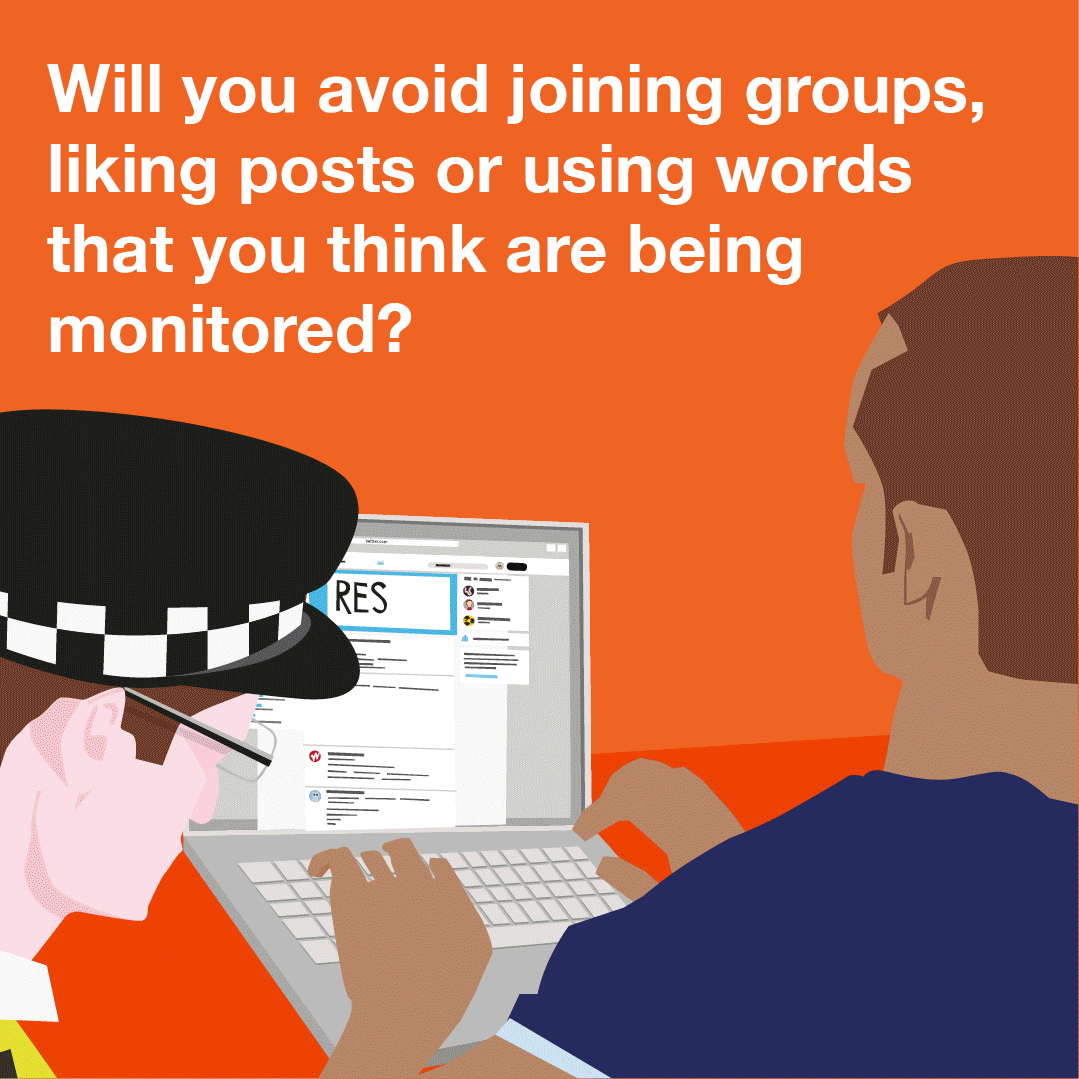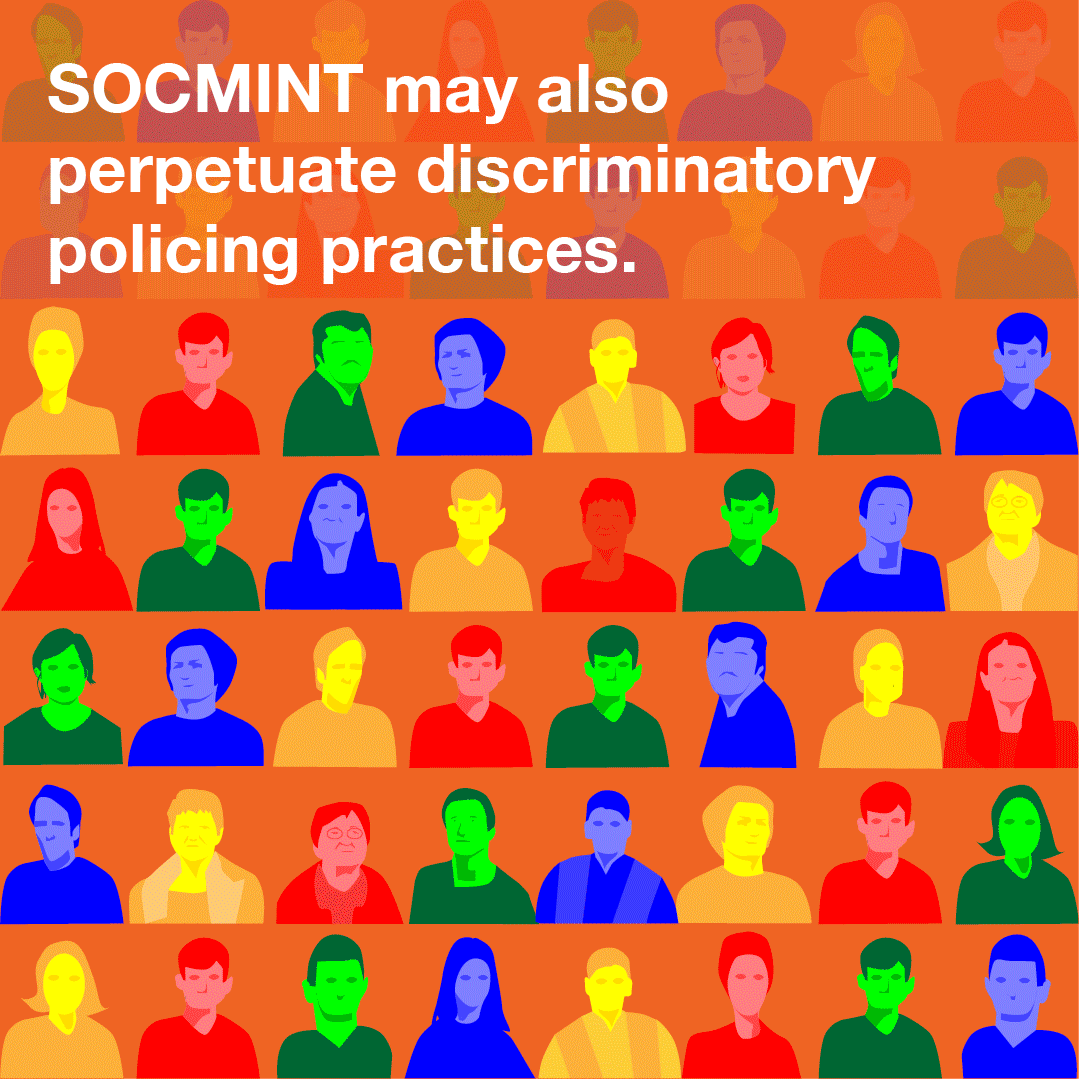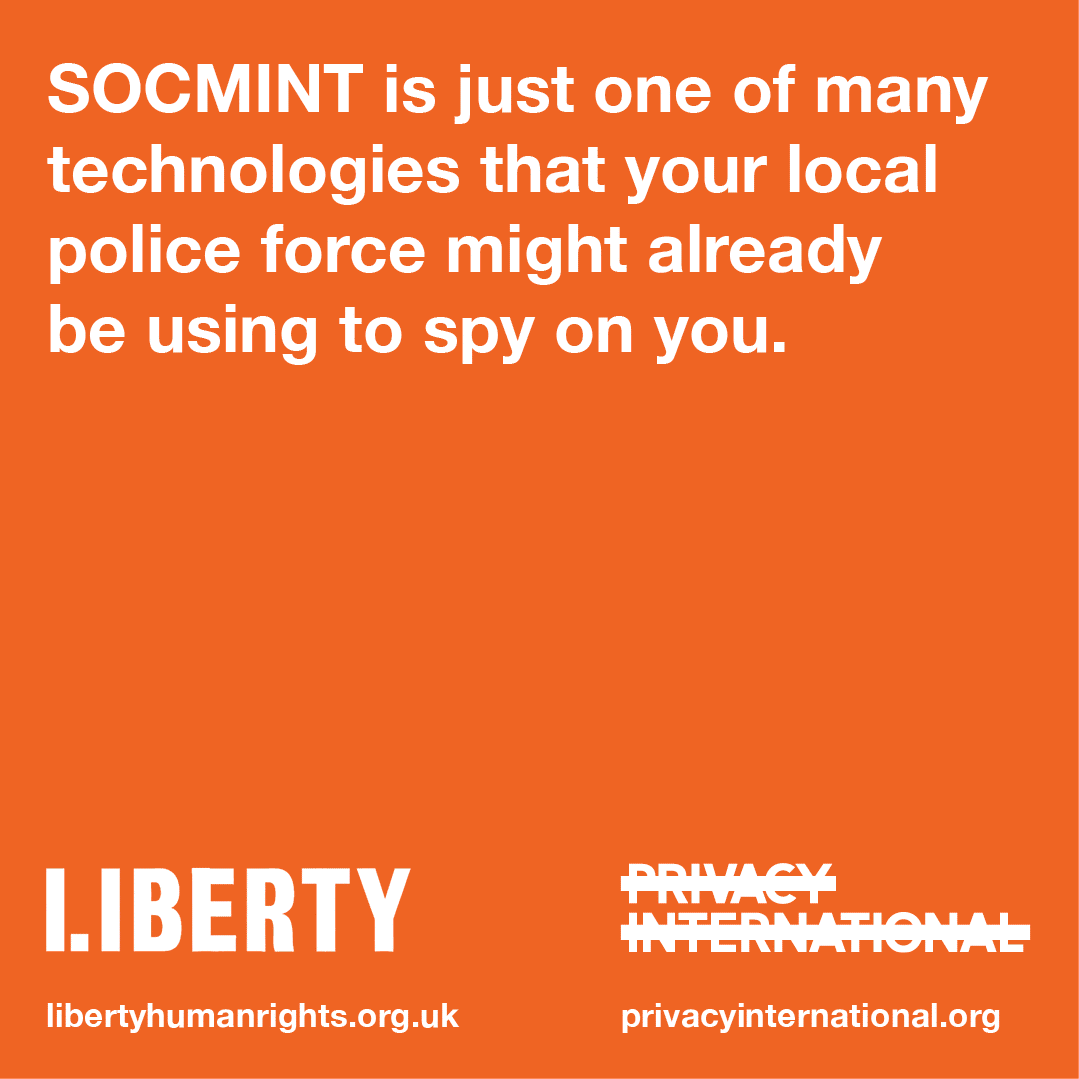
Content Type: Explainer graphic
You can also read a more detailed explainer about social media intelligence (SOCMINT) here.
Content Type: News & Analysis
At Privacy International, we talk about: “the world being on fire.”We say it to talk about the recurring threats to our democracies, the elections of authoritarian leaders, the current political climate… Or the actual climate. More often than not, we use it to talk about the (lack of) security in the design and implementation of computer systems.
But there is another kind of fire. The fourth wave of feminism – the one that contributed to the protests following the 2012 gang rape of…
Content Type: News & Analysis
Image source: Oxfam
This piece was co-authored with Ruhiya Seward, Senior Program Officer at IDRC and originally appeared here.
What if in trying to make development more equitable we’re creating risks that disproportionately impact people based on their gender?
Development programming aims to be both sustainable and equitable in part by recognizing the implications of inequality in its many forms, whether by gender, ethnicity, socioeconomic status, or geolocation. The adoption of the…
Content Type: Video
Video courtesy of CPDP (https://www.cpdpconferences.org/)
What is the impact of online gender-based violence on survivors? What should be the role of companies in fighting this phenomenon? What is the link between the right to privacy? In this panel, which took place at CPDP in February 2019, academics, civil society and government representatives discuss the issue of online gender based violence with a privacy lens.
Chair: Gloria González Fuster, VUB -LSTS (BE)
Moderator: Valerie…
Content Type: Long Read
For International Women’s Day 2019, Privacy International looks at some of the key themes around the intersection of gender rights and the right to privacy and we review the work we and our partners have done on those topics.
When dealing with cases of non-consensual sharing of intimate images, often known as ‘revenge porn,’ or doxxing, where a person’s personal details are shared publicly, the link between privacy and online-gender-based violence is very clear. Privacy…
Content Type: News & Analysis
Creative Commons Photo Credit: Source
In this first episode of the Gender and Privacy Series, we go to Manila in the Philippines to meet two transgender right activists - Naomi Fontanos and AR Arcon. We discuss what the right to privacy means to them and their fight against the government's plan to deploy an ID card system.
Listen to the podcast here.
Content Type: News & Analysis
Creative Commons Photo Credit: Source
In the third episode of the Gender and Privacy Series, we talk about sex and privacy with two female activists: Sarah Jamie Lewis, an expert on the security of internet-connected sex toys, and Joana Varon, founder of the female-led Brazilian NGO Coding Rights.
Listen to the podcast here.
Content Type: Report
Whose privacy are we fighting for when we say we defend the right to privacy? In this report we take a hard look at the right to privacy and its reality for women, trans and gender diverse people. We highlight how historically privacy has been appropriated by patriarchal rule and systems of oppression to keep women, trans and gender diverse people in the private sphere.
For us, this report is also an opportunity to show how surveillance and data exploitation are also uniquely affecting…