Advanced Search
Content Type: Case Study
The increasing deployment of highly intrusive technologies in public and private spaces such as facial recognition technologies (FRT) threaten to impair our freedom of movement. These systems track and monitor millions of people without any regulation or oversight.
Tens of thousands of people pass through the Kings Cross Estate in London every day. Since 2015, Argent - the group that runs the Kings Cross Estate - were using FRT to track all of those people.
Police authorities rushed in secret…
Content Type: Long Read
The UK’s Metropolitan Police have began formally deploying Live Facial Recognition technology across London, claiming that it will only be used to identify serious criminals on “bespoke ‘watch lists’” and on “small, targeted” areas.
Yet, at the same time, the UK’s largest police force is also listed as a collaborator in a UK government-funded research programme explicitly intended to "develop unconstrained face recognition technology", aimed “at making face…
Content Type: Case Study
In 2015, James Bates was charged with first-degree murder in the death of Victor Collins. Collins was found floating face down in Bates’ hot tub in November 2015. Bentonville police served two search warrants ordering Amazon to turn over the “electronic data in the form of audio recordings, transcribed records, text records and other data contained on the Amazon Echo device” in Bates’ home.
The reason for the warrants? According to the police, just because the device was in the house that…
Content Type: Long Read
In 2018, following the Cambridge Analytica scandal, Facebook announced the “Download Your Information” feature allowing users to download all the information that the company have on them since the creation of the account. All of it? It doesn’t seem so. Concerns were quickly raised when Facebook released the feature, that the information was inaccurate and incomplete.
Privacy International recently tested the feature to download all ‘Ads and Business’ related information (You can accessed it…
Content Type: Case Study
Anyone who is arrested should be informed of the reasons for their arrest and any charges against them. Anyone who is detained is also entitled to a trial within a reasonable time, or to be released if no charges are held against them.
Privacy enhances these protections. It provides limitations on the manner in which information can be obtained about you, and the kind of information that can be accessed about you by law enforcement, who can access that information and how they can use it.…
Content Type: Report
The changes discussed in this article are based on a second analysis performed in late November, 3 months after the original study Your Mental Health is for Sale and following the exact same methodology. All data collected can be found at the bottom of this page.
Change is possible
Back in September 2019 we published the report Your Mental Health is for Sale exposing how a majority of the top websites related to mental health in France, Germany and the UK share data for advertising purposes.…
Content Type: Long Read
It was a quiet evening in Agadez, a bustling Saharan city in the centre of Niger. Thirty-five year old Agali Ahmed was sipping tea at a friend’s place, as he often did, when he received a message: police were at his uncle’s house. When he got there, Ahmed saw men in plainclothes, standing around the building’s gate. Inside, more men were searching the apartment. Three white men, who Ahmed guessed were Spanish, asked for his phone and started taking pictures of him. They told him to follow them…
Content Type: Video
In this podcast Sara Nelson of PI’s Reproductive Rights and Privacy Project talks about the US based international anti-abortion organisation Heartbeat International and the technologies they are developing for their international network of affiliate organisations. We also discuss what reproductive rights are and why PI is working on the topic:
Music by Glass Boy, find more of their work here: glassboy.bandcamp.com/album/enjoy (creativecommons.org/licenses/by-nd/3.0/)
Content Type: Long Read
We are excited to spotlight our Reproductive Rights and Privacy Project!
The Project is focused on researching and exposing organisations that collect and exploit the information of those seeking to exercise their reproductive rights. Working together with PI partners, other international grassroots organisations and NGOs, PI is researching and advocating against this data exploitation.
So, what are reproductive rights?
Sexual and reproductive rights, which are contained within Economic,…
Content Type: Long Read
The European Union (EU) spends billions on research and development aimed at driving economic growth and jobs, as well as furthering the bloc’s broader agenda. Within the current budget, known as Horizon 2020 and covering the years 2014-2020, some €80 billion has been made available for research in a huge number of areas, ranging from finding cures for diseases to helping keep the earth viable for life.
From the same budget, it also funds a lot of projects aimed at developing surveillance…
Content Type: News & Analysis
Privacy shouldn’t be a luxury.
Google claim to agree with us - we know that because Sundar Pichai, their CEO, said so this May in the New York Times. And yet, Google are enabling an ecosystem that exploits people who own low-cost phones.
Today we, along with over 50 organisations including Amnesty International, DuckDuckGo, and the ACLU are asking Google to step up, and we’re asking you to join us in pressuring them to do the right thing.
Sign the petition
Google has the power to…
Content Type: News & Analysis
Cloud extraction allows law enforcement agencies to take huge amounts of your data from the Cloud via a legal back door. If law enforcement seize your phone or take it from a victim of crime, they can extract tokens or passwords from the device which lets them get access to data from apps such as Uber, Instagram, Slack, Gmail, Alexa and WhatsApp.
In so doing, law enforcement agencies can avoid official channels through cloud companies such as Google, Apple…
Content Type: Press release
A large number of apps on smart phones store data in the cloud. Law enforcement can access these vast troves of data from devices and from popular apps with the push of a button using cloud extraction technology.
Mobile phones remain the most frequently used and most important digital source for law enforcement investigations. Yet it is not just what is physically stored on the phone that law enforcement are after, but what can be accessed from it, primarily data stored in the Cloud.…
Content Type: Long Read
Following a series of FOI requests from Privacy International and other organisations, the Department of Health and Social Care has now released its contract with Amazon, regarding the use of NHS content by Alexa, Amazon’s virtual assistant. The content of the contract is to a big extent redacted, and we contest the Department of Health’s take on the notion of public interest.
Remember when in July this year the UK government announced a partnership with Amazon so that people would now…
Content Type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content Type: Long Read
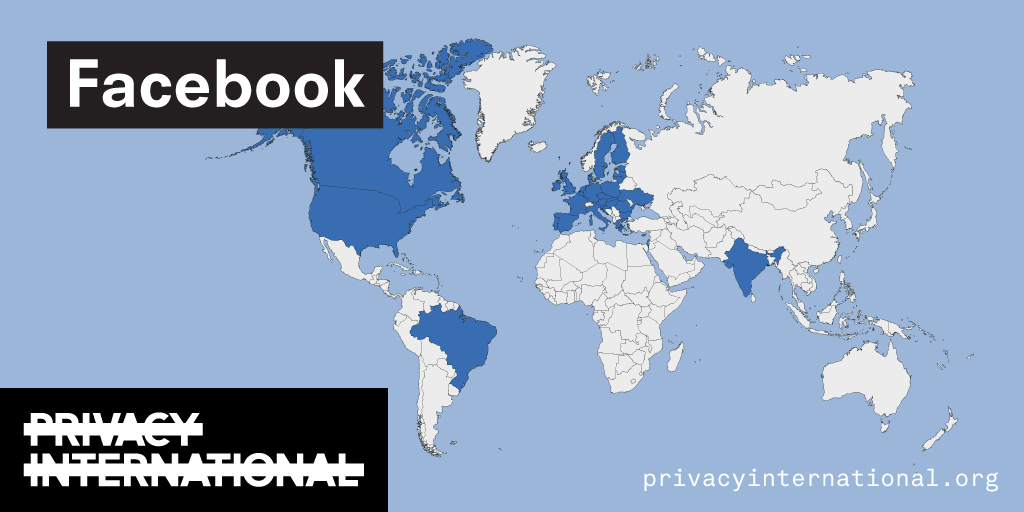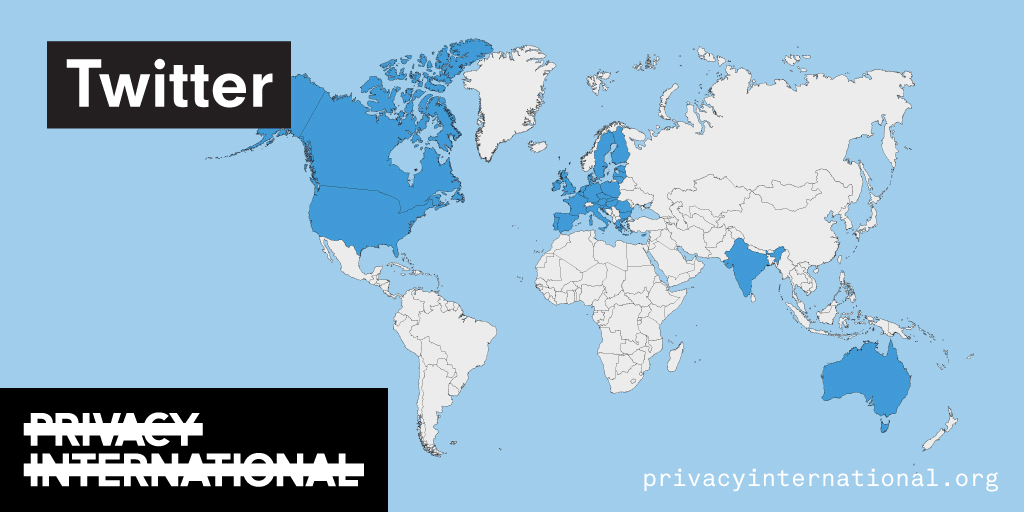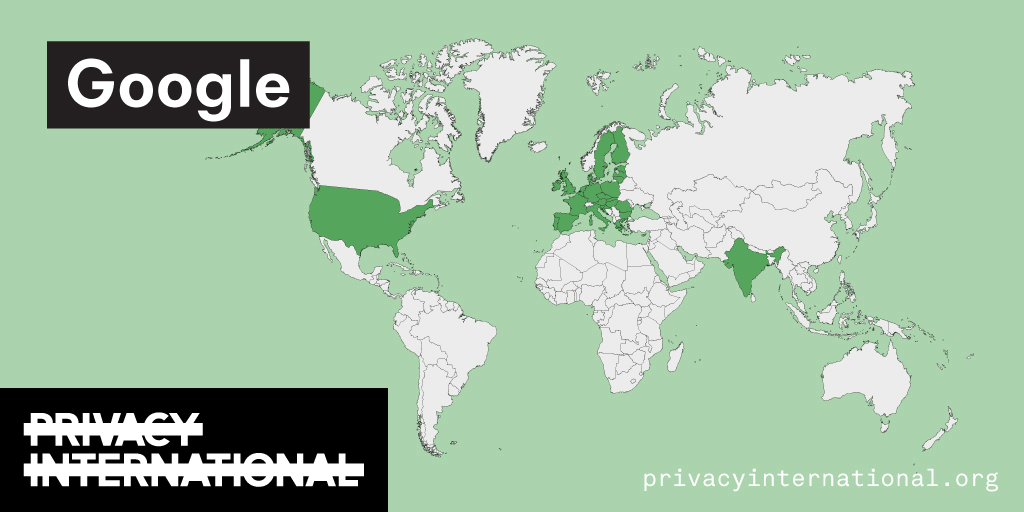
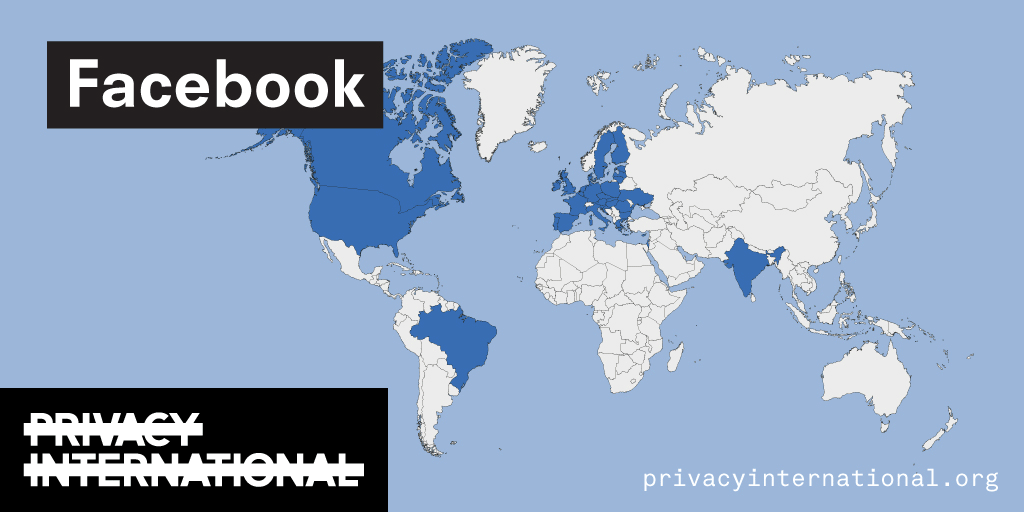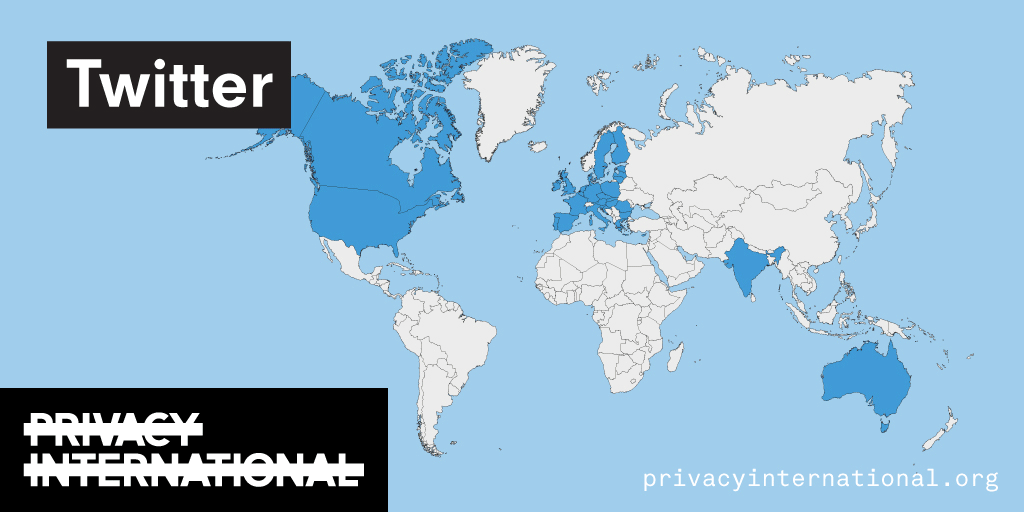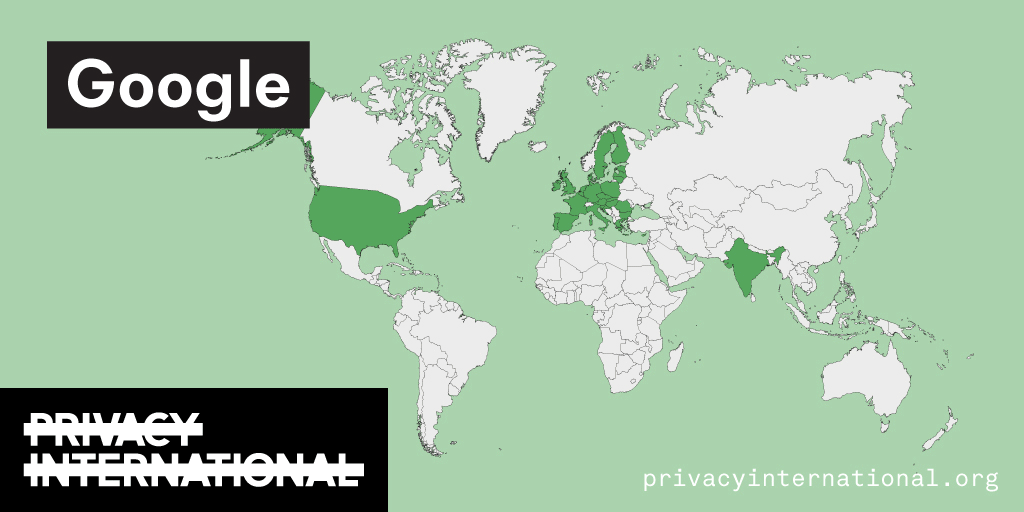
An analysis of what Facebook, Google, and Twitter have done to provide users with political ad transparency as of September 2019. Our full analysis is linked below.
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign entities, and more. Significant…
Content Type: Long Read
Content Type: Video
Christopher Weatherhead and Eva Blum-Dumontet Discuss the finding of Privacy International's report on the MyPhone MYA2 from the Philippines
Content Type: Long Read
In December 2018, Privacy international exposed the dubious practices of some of the most popular apps in the world.Out of the 36 apps we tested, we found that 61% automatically transfer data to Facebook the moment a user opens the app. This happens whether the user has a Facebook account or not, and whether they are logged into Facebook or not. We also found that some of those apps routinely send Facebook incredibly detailed and sometimes sensitive personal data. Again, it didn’t matter if…
Content Type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content Type: Long Read
Cellebrite, a surveillance firm marketing itself as the “global leader in digital intelligence”, is marketing its digital extraction devices at a new target: authorities interrogating people seeking asylum.
Israel-based Cellebrite, a subsidiary of Japan’s Sun Corporation, markets forensic tools which empower authorities to bypass passwords on digital devices, allowing them to download, analyse, and visualise data.
Its products are in wide use across the world: a 2019 marketing…
Content Type: State of Privacy
Introduction
Acknowledgment
The State of Surveillance in Tunisia is the result of an ongoing collaboration by Privacy International and partners.
On 14 February 2023, the United Nations High Commissioner for Human Rights voiced concern over the deepening crackdown in Tunisia targeting perceived political opponents of President Kais Saied as well as civil society.
We have updated this page to reflect important changes in the state of surveillance in Tunisia.
Key privacy facts
1.…
Content Type: News & Analysis
In December 2018, we revealed how some of the most widely used apps in the Google Play Store automatically send personal data to Facebook the moment they are launched. That happens even if you don't have a Facebook account or are logged out of the Facebook platform (watch our talk at the Chaos Communication Congress (CCC) in Leipzig or read our full legal analysis here).Today, we have some good news for you: we retested all the apps from our report and it seems as if we…
Content Type: News & Analysis
Campaigners are today calling for urgent action to allow Palestinians to develop an independent telecommunications infrastructure following the release of a report detailing how the Israeli government exerts its existing control to rule and monitor the online lives of Palestinian people.
‘Connection Interrupted’, produced by Privacy International partner organisation 7amleh, describes how the Israeli government restricts key telecommunications infrastructure in Palestine,…
Content Type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgement
The State of Privacy in Uganda is the result of an ongoing collaboration by Privacy International and Unwanted Witness.
Key privacy facts
1. Constitutional privacy protection: The constitution contains an explicit protection of the right to privacy (Art. 27).
2. Data protection law: There is no…
Content Type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgment
The State of Privacy in South Africa is the result of an ongoing collaboration by Privacy International and the Right2Know coalition.
Key Privacy Facts
1. Constitutional privacy protections: Section 14 of the Constitution of the Republic of South Africa protects the right to privacy.
2. Data protection laws…
Content Type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgement
The State of Privacy in the Philippines is the result of an ongoing collaboration by Privacy International and Foundation for Media Alternatives.
Key privacy facts
1. Constitutional privacy protection: The constitution contains an explicit protection of the right to privacy (Art. III, section 3).
2.…
Content Type: State of Privacy
Table of contents
Introduction
Right to Privacy
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgment
The State of Privacy in Pakistan is the result of an ongoing collaboration by Privacy International and the Digital Rights Foundation.
Between 2014-2016, Bytes for All contributed to previous versions of the 'Data Protection' sections of this briefing.
Key Privacy Facts
1. Constitutional privacy protections: Article 14(1) of…
Content Type: State of Privacy
Table of contents
Introduction
Right to Privacy
Communication Surveillance
Data Protection
Identification Schemes
Policies and Sectoral Initiatives
Introduction
Acknowledgment
The State of Surveillance in Morocco is the result of an ongoing collaboration by Privacy International and its partners.
Key privacy facts
1. Constitutional privacy protection: The constitution contains an explicit protection of the right to privacy.
2. Data protection law: There is a data…