Search
Content type: News & Analysis
Trade has often been a positive driver in encouraging countries to adopt data protection laws, to ensure compliance and ability to conduct business with the European Union and other privacy-respecting partners. However, when free trade agreements are negotiated in secret and influenced by powerful business interests, the result is a severe watering down of existing privacy protections.
There is a high risk of this happening in the free trade negotiations between the European Union…
Content type: News & Analysis
Below is an excerpt of an article that recently appeared in Melbourne, Australia's The Age, written by Carly Nyst, Head of International Advocacy at Privacy International:
"Mass surveillance of a country's citizens by its government can no longer be said to be the preserve of authoritarian and dictatorial states.
The publication last week by The Guardian of classified National Security Agency documents has exposed the extent of surveillance by the US government, throwing into question…
Content type: Long Read
Spy agencies have long sought to turn the technologies that improve all our lives against us. From some of the very first forms of remote communications such as telegraph cables, to modern-day means like Skype: if the spies can exploit it, they will.
And, as we’ve learnt over the last few months, the computer and mobile devices that millions of us own and carry around with us every day are no exception to this rule.
The smart phones, laptops, and devices that have changed how we communicate…
Content type: News & Analysis
This post originally appeared on the blog for Association for Progessive Communications, written by Shawna Finnegan and Carly Nyst, for APCNews and Privacy International:
At the 23rd session of the UN Human Rights Council, the UN Special Rapporteur on freedom of opinion and expression, Frank La Rue, released his latest report – an analysis of the implications of States’ surveillance of communications on the exercise of the human rights to privacy and to freedom of opinion and expression.…
Content type: News & Analysis
UPDATE: The Guardian has just reported that "The UK's electronic eavesdropping and security agency, GCHQ, has been secretly gathering intelligence from the world's biggest internet companies through a covertly run operation set up by America's top spy agency."
This recent news reveals a long-held suspicion that the GCHQ had the very powers they were seeking to place on a statutory footing with the Snooper Charter, a bill that was knocked back for being unnecessary and…
Content type: News & Analysis
The revelations of the US government's massive and indiscriminate surveillance program are absolutely frightening, putting before the public's eyes the breadth of a secret, dragnet spying regime which casts every US citizen as a suspect.
The unearthing of this top secret court order shows that even in a country that prides itself on checks and balances, and is governed by the rule of law, that government and law enforcement agencies operate within a murky legal framework…
Content type: News & Analysis
A longer version of this article was previously published in Wired on 10 May 2013.
We all know surveillance is big in Putin’s Russia. What you may not know is that Russia’s surveillance tech is being used all over the world, even in the U.S.
The Kremlin is up to its domes in spy technology. One reason is fear, provoked by the Arab Spring, of a growing and diffuse protest movement that uses social media to organize. Notably, the authorities have taken an interest in DPI (…
Content type: News & Analysis
After a successful investigation by the US government into the illegal reselling of over a million dollars worth of surveillance equipment to the Syrian regime, Dubai distribution company Computerlinks FZCO has agreed to pay the maximum civil penalty of $2.8 million.
Computerlinks, in three separate transactions between October 2010 and May 2011, sold $1.4 million worth of devices developed by California-based Blue Coat to the state-run Syrian Telecommunications Establishment, which…
Content type: Press release
A European privacy group claimed today that dozens of amendments to the new Data Protection Regulation being proposed by Members of the European Parliament (MEPs) are being copied word-for-word from corporate lobby papers, with MEPs frequently failing to even remember their own amendments. Max Schrems, of the website and campaign Europe v Facebook, noticed striking similarities between proposed amendments and lobby papers written by representatives of Amazon, eBay, the American Chamber of…
Content type: News & Analysis
On International Data Privacy Day, it is important that we all ask ourselves: who has access to our personal information? Who can find out where we’ve been and who we’ve called, who can read our emails and our text messages? Who can find which websites we access and which files we download?
Statistics released by Google and Twitter over the past week are a sobering reminder that it is not only the corporations to which we consensually provide this information which are able…
Content type: Press release
Google's latest Transparency Report, released at 3pm GMT this afternoon, shows that requests by European governments for the browsing history, email communications, documents and IP addresses of Google's users have skyrocketed since the Transparency Report was launched three years ago. Countries in the European Union made 7,254 requests about 9,240 users or accounts between July and December 2012, averaging over 1,200 requests a month. This represents over a third of all requests made by…
Content type: News & Analysis
Last month, US District Judge William Griesbach ruled that police can lawfully install covert digital surveillance cameras on private property without a warrant. Officers of the Drug Enforcement Agency had entered a property belonging to Marco Magana, which was littered with ‘no trespassing’ signs and behind a locked gate, and installed hidden cameras without the consent or knowledge of either the occupant or a court of law. In what has been described by Salon as “yet another…
Content type: News & Analysis
Privacy International is proud to announce our new project, Eyes Wide Open, which aims to pry open the Five Eyes arrangement and bring it under the rule of law. Read our Special Report "Eyes Wide Open" and learn more about the project below.
For almost 70 years, a secret post-war alliance of five English-speaking countries has been building a global surveillance infrastructure to “master the internet” and spy on the worlds communications. This arrangement binds together the US, UK, Canada,…
Content type: News & Analysis
Privacy International asked lawyers, activists, researchers and hackers at Defcon 2012 about some of the debates that thrive at the intersection between law, technology and privacy. We also wanted to know why privacy matters to them, and what they thought the future of privacy looked like. This video is a result of those conversations.
Featuring Cory Doctorow, Kade Crockford, Jameel Jaffer, Dan Kaminsky, Chris Soghoian, Marcia Hoffman, Moxie Marlinspike, Phil Zimmerman, Hanni Fakhoury…
Content type: News & Analysis
Tuesday’s letter to Google CEO Larry Page, personally signed by 29 European data protection authorities, ordered the corporation (inter alia) to give users greater control over their personal information. The notions of trust and control are emphasised throughout the letter, and Google is urged to "…develop new tools to give users more control over their personal data" and "collect explicit consent for the combination of data for certain purposes". It is good news that the…
Content type: News & Analysis
APEC privacy activity has passed another milestone with the acceptance in July 2012 of the USA as the first economy to formally join the cross border privacy rules (CBPR) system. The CBPR Joint Oversight Panel (JOP), with the Canadian chair of the Data Privacy Subgroup (DPS) standing in for the US member in accordance with the ‘no conflict of interest’ provisions, accepted the US government application, which nominated the Federal Trade Commission (FTC) as the privacy enforcement authority…
Content type: News & Analysis
The Home Office constantly insists that trafffic data is not about the content of the pages you look at, but about the sites you visit.
This would have made some sense in 1999 when RIPA was first being debated, but technology has moved on and new open data sources are now available. This allows for vastly more invasive tracking in 2012 than was envisaged in 2000. We’ve done a little bit of work on how…
The English Wikipedia contains 4 million articles, which contain 18 million links out…
Content type: News & Analysis
As part of Privacy International's investigation into the mass surveillance industry we have examined hundreds of legal documents, brochures and, most recently, patents. Patents are a form of intellectual property; patent-holders publicly disclose their inventions in exchange for the exclusive rights to use and commercialise them for a limited period of time. Patent registries therefore provide a window into the otherwise murky world of the mass surveillance industry.
We believe…
Content type: News & Analysis
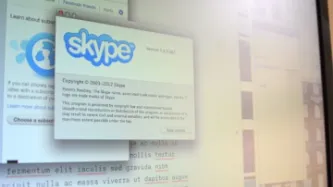
The recent acquisition of Skype by Microsoft, coupled with a series of infrastructural changes, has resulted in a flurry of responses, concerns and analysis of exactly what kind of assistance Skype can provide to law enforcement agencies. Under this heightened scrutiny, Skype released a statement on their blog on 26th July, purporting to re-affirm their commitment to the privacy of their users.
Privacy International are delighted to read that Skype believes that…
Content type: News & Analysis
Last Friday the Electronic Frontier Foundation received new information from the US Federal Aviation Administration in response to their FOIA demanding data on certifications and authorizations the agency has issued for the operation of unmanned aircraft.
The information includes extensive details about the specific drone models currently flying in US civilian airspace, including those being used by four local police forces. The North Little Rock Police Department in Arkansas is…
Content type: News & Analysis
The APEC Data Privacy Subgroup (DPS) commenced a new five year work programme at a meeting in Moscow in February 2012. This follows the commitment by APEC Leaders in late 2011 to the Cross Border Privacy Rules (CBPR) system as one way implementing the APEC Data Privacy Framework.
The Joint Oversight Panel was formed at the DPS meeting in Moscow and comprises members from the US (chair), Chinese Taipei and Mexico, with the chair of the DPS (from Canada) as alternate – who will…
Content type: Report
The US does not have a general overarching privacy law like European Data Directive or the sweeping privacy protections contained in the European declarations of rights. The EU-US accord cites several laws, which it claims, give privacy rights to non-US persons. None of the cited laws offer any real substantive or procedural protections for Europeans. As explained below, the one law – the Privacy Act 5 U.S.C 552a – that could offer some modest protections is tellingly not even mentioned.
But…
Content type: Report
This is a memo prepared by Barry Steinhardt of Friends of Privacy USA for Members of the European Parliament regarding the proposed EU-US Agreement PNR.
The proposed agreement regarding Passenger Name Records (PNR) between the United States and the European Union is riddled with faulty assertions and assumptions about US law and the actual operations of the US government.
These faulty assertions and assumptions go to the heart of the agreement and undercut the claims of protections for…
Content type: News & Analysis
Last month, within thirty seconds of the BBC publishing a quotation from me on the latest round of the nymwars and Google+, my phone rang. Caller ID indicated that it was someone I know who works at Google. "Had I said something wrong?" was my first thought. I quickly retraced in my mind what it was that I had said to the journalist; I had responded in the article that Google's recent announcement could be seen as positive but really it was a sidestepping of the larger challenge of identity…
Content type: Press release
In collaboration with the Wall Street Journal and the Guardian, Privacy International today published a database of all attendees at six ISS World surveillance trade shows, held in Washington DC, Dubai and Prague between 2006 and 2009. ISS World is the biggest of the surveillance industry conferences, and attendance costs up to $1,295 per guest. Hundreds of attendees are listed, ranging from the Tucson Police Department, to the government of Pakistan, to the International…
Content type: News & Analysis
Independent security researcher Trevor Eckhart revealed yesterday that a recent software update to some HTC smartphones has accidentally given third party applications access to huge amounts of private data, including call logs, geolocation history, SMS data and a whole lot more.
The update surreptitiously installs a suite of applications logging users' interactions with their devices. When a device is first switched on, the user ostensibly has the option not to allow HTC to…
Content type: News & Analysis
The second 2011 meeting of the APEC Privacy Subgroup took place in San Francisco in mid September, and finalised the package of documents that comprise the Cross Border Privacy Rules (CBPR) system. Endorsed by the parent Electronic Commerce Steering Group (ECSG), these will now go forward for ratification by Ministers in Hawaii in November, and subsequent implementation. The Subgroup’s 2012 Work Plan envisages establishment of the Joint Oversight Panel (JoP), commencement of…
Content type: News & Analysis
Other human rights organisations often ask us what they should to when it comes to their infosec needs. Should they run their own mail server, or trust Gmail? Should they merge their calendars by email (!), a local server, or use some cloud solution?
We honestly don't know what to tell them. In fact, we are unsure of what we ourselves should be doing. We know that there are risks of keeping things local (e.g. lack of redundancy), and there are risks of data being stored…
Content type: News & Analysis
2011 is supposed to be the year that the APEC pathfinder projects on Cross Border Privacy Rules (CBPR) deliver a functional system for businesses to be certified for transfer of personal information between participating APEC economies.
After the last round of APEC privacy meetings in Washington DC on 1-3 March, this prospect is looking increasingly remote. Even the basic set of documentation and processes required for the process of self-certification and assessment of businesses has yet to…
Content type: News & Analysis
Skype has consistently assured that it protects its users and their communications. Having reviewed the company's technology and policies we have grounds for concern about Skype's overall level of security, and we believe there are a number of questions to which the company must respond. Skype's misleading security assurances continue to expose users around the world to unnecessary and dangerous risk. It's time for Skype to own up to the reality of its security and to take a leadership…