Five Eyes Integration and the Law
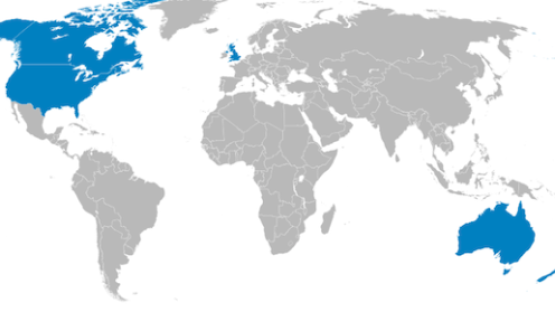
Few revelations have been been as troubling for the right to privacy as uncovering the scope of the Five Eyes alliance. The intelligence club made up of Australia, Canada, New Zealand, the United Kingdom and the United States has integrated its collection efforts, staff, bases, and analysis programs. Yet the legal rulebook governing how the agencies ensure the most comprehensive joint surveillance effort in the history of mankind remains secret.
The little that is known suggests a disappointing state of affairs in which operational effectiveness has trumped everything else, reducing critical questions of cross border legality to self-assessed tests, check boxes, and drop down menus.
A history of data sharing
The Five Eyes have been co-operating since 1946. It has been believed for some time that much of the intelligence produced by the Five Eyes can be accessed by any of the partner states at any time. As early as the 1980’s, ECHELON, a “global Internet-like communication network,” allowed Five Eyes analysts to “task computers at each collection site, and receive the results” on civil satellite communications.
It is likely that the Five Eyes agencies have adopted common approaches to collection and similar interfaces as means of making intelligence co-operation and sharing more expedient. Yet agencies in different member states operate under disparate systems of laws and practice, making some effort to harmonize such standards beneficial given the functional integration and co-operation across the Five Eyes.
How complex legal disparities have been resolved to ensure respect for each state's legal framework has long remained in the shadows. Thanks to Edward Snowden, and recent EFF and ACLU Freedom of Information Act litigation, we are beginning to see that lack of adequate legal compliance may be much more far-reaching than we initially dared to imagine.
Expediency?
In a recently revealed NSA screenshot, at the very bottom of the interface for the NSA “Unified Targeting Tool,” which records rationales for targeting individuals, an 'HRA compliant' option has been included. This compliance box, likely to refer to the British Human Rights Act of 1998, has no legal relevance for an NSA analyst unless the NSA plans to share intelligence obtained with the UK. Similar terminology also occurs in the recent leaks regarding sim card hacking where “HRA justifications" are required to be entered to access the database of SIM card encryption keys stolen by GCHQ. The inclusion of 'HRA compliant' suggests tools are built with a nod to UK legal compliance in an attempt to ensure the exchange of intelligence on individuals is more expedient.
Unified tasking, and sharing tools.
A series of screenshots suggest that the Five Eyes partners have adopted similar interfaces, justifications and legal compliance procedures for tasking and prioritization, too. What is perhaps most striking is that many screenshots show the use so-called “Miranda” numbers.
The Intercept first published screenshots of GCHQ analyst interfaces that include reference to Miranda as an “administrative interface that GCHQ uses to store details about information desired by its government 'customers.'” Until recently, we considered Miranda a British intelligence database feature. However, with the appearance of references to Miranda by multiple parties to the Five Eyes alliance, this interface appears to play some international co-ordination function, too. Remarkably, the drop-down menus don't merely occur among the core Five Eye parties; third parties such as Sweden are also using the same system.
Multiple choice
In order to access the many shared and integrated databases created by the Five Eyes, analysts simply need to undertake self-learning and self-assessment tests.
One internal document shows that for Five Eyes analysts to search through New Zealand XKEYSCORE databases, they need to access a system called “iLearn” and undertake a “NZSID7” legal briefing. According to the same document, similar legal briefings exist for the United Kingdom and for the United States in the form of “HRA” and “USSID-SP0018” training.
These tests are "multiple choice, open-book" tests done at the agent's own desk on the "iLearn" system with no external assessment. If the analyst decides they've passed, they have to “copy and paste the results into a word document” before clicking through to whatever shared database they wish.
Categorization as a means of legal justification?
Internal training documents show that Five Eyes analysts are presented with simple interfaces to query the large volume of private communications they have intercepted. To look up all the historic emails corresponding to a target's email addresses, analysts simply have to select a start and end date, and type in an email address or subject of the email. This search will return every email address GCHQ (and possibly some Five Eyes partners) has ever collected and stored that match the search terms.
For this search to be “legal”, additional information is required. Analysts are presented with two boxes to fill in and the option to select from a drop down menu.
In one screenshot, the example justification is “ct target in n africa”, which presumably is shorthand for “counter-terrorism target in north Africa.” This kind of shorthand example is common, with other screenshots showing the justification as “aqi in iran sample”, presumably referring to Al-Qaeda in Iran. The target is described as “abujihad”. It is regrettable that GCHQ’s trainers use such crude stereotypes in their training materials, which are designed to evidence the seriousness and care with which they justify serious intrusions on privacy.
Operational effectiveness comes first
Almost two years after Snowden, the governments of the Five Eyes continue to dodge questions of how the integration of the Five Eyes is legally sufficient. Key documents like the Five Eyes arrangement remain secret, despite them being critical to proper scrutiny of the spy agencies.
Thanks to Edward Snowden, we know the Five Eyes have integrated programmes, integrated staff, integrated bases, and integrated analysis. Yet despite this, the legal rulebook ensuring the most comprehensive surveillance effort in the history of mankind is consistent with human rights appears to extend to nothing more than recording self assessed scores from a multiple choice open book test in a word document and a few drop down menus.



