Search
Content type: News & Analysis
On 24 October 2019, the Swedish government submitted a new draft proposal to give its law enforcement broad hacking powers. On 18 November 2019, the Legal Council (“Lagråd”), an advisory body assessing the constitutionality of laws, approved the draft proposal.
Privacy International believes that even where governments conduct hacking in connection with legitimate activities, such as gathering evidence in a criminal investigation, they may struggle to demonstrate that hacking as…
Content type: News & Analysis
In the last few months strong concerns have been raised in the UK about how police use of mobile phone extraction dissuades rape survivors from handing over their devices: according to a Cabinet Office report leaked to the Guardian, almost half of rape victims are dropping out of investigations even when a suspect has been identified. The length of time it takes to conduct extractions (with victims paying bills whilst the phone is with the police) and the volume of data obtained by the…
Content type: News & Analysis
Yesterday, we found out that Google has been reported to collect health data records as part of a project it has named “Project Nightingale”. In a partnership with Ascension, Google has purportedly been amassing data for about a year on patients in 21 US states in the form of lab results, doctor diagnoses and hospitalization records, among other categories, which amount to a complete health history, including patient names and dates of birth.
This comes just days after the news of Google'…
Content type: Long Read
Miguel Morachimo, Executive Director of Hiperderecho. Hiperderecho is a non-profit Peruvian organisation dedicated to facilitating public understanding and promoting respect for rights and freedoms in digital environments.The original version of this article was published in Spanish on Hiperderecho's website.Where does our feeling of insecurity come from? As we walk around our cities, we are being observed by security cameras most of the time. Our daily movement, call logs, and internet…
Content type: News & Analysis
Even if we are not Fitbit users, we all need to stop and think about the implications of this merger. There is a reason that our health data is subject to higher levels of protection - its intimate, reveals vast amounts about our everyday lives, and the potential consequences if exploited can be devastating. Google should be keeping its hands off our health data.
Sign our letter to the European Commission, asking them to block the Google/Fitbit merger.
Let's tell Google, 'NOT ON OUR WATCH!'
Content type: Long Read
Sitting on the ground inside an unadorned courtyard in Koira Tegui, one of Niamey’s most popular districts, Halimatou Hamadou shows a copy of what, she’s been told, is a certificate of birth.
The 33 year old woman, who’s unable to read and write, received it days earlier during a crowded public ceremony at a nearby primary school.
“It’s my first document ever,'' she says, with surprise.
Thanks to the paper, she’ll be able to take part in a crucial passage for the future of Niger: the…
Content type: Press release
Privacy International, Open Rights Group, the Institute for Strategic Dialogue, Fair Vote, Who Targets Me? and Demos have today written to all the main UK political parties, demanding that they are transparent with the public about how they are using voters’ personal data in their electioneering. Twitter's announcement yesterday of their ban on political advertising is just the latest wake up call to politicians about the risks to democracy of personal data driven microtargeting of political…
Content type: News & Analysis
Privacy International has been doing work on the UK-based digital identity company, Yoti. We have raised concerns about their use of user data for their 'Yoti Age Scan' product. As we say in our analysis:
Yoti Age Scan is just one example of digital identity. The issues ... can be used to reflect on wider issues relating to the use of data gathered in the course of identity services: how do we want the identity industry to treat our data? What is the future for this market, and how do we…
Content type: Long Read
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge…
Content type: News & Analysis
CC: BY (Kirill Sharkovski)-SA
Este artículo fue escrito por Jamila Venturini, Coordinadora regional de Derechos Digitales. El artículo fue publicado por primera vez aquí. This article is available in English.
La implementación de programas que condicionan el acceso a servicios básicos por medio de vigilancia estatal y privada agudizan la inequidad imperante en el continente.
Mientras la brecha entre ricos y pobres se incrementa en el mundo, América Latina sigue siendo la región donde la…
Content type: News & Analysis
Picture: CC: BY (Kirill Sharkovski)-SA
This article was written by Jamila Venturini from Derechos Digitales. The original version (in Spanish) is available here.
How implementing social protection programmes that condition access to basic services to state and private surveillance exacerbate the prevailing inequality on the continent.
While the gap between rich and poor is increasing in the world, Latin America remains the most unequal region of the world. According to the Economic…
Content type: News & Analysis
Photo by Ray Witlin / World Bank CC BY-NC-ND 2.0
This article has been written by Ambika Tandon, Policy Officer at the Centre for Internet and Society, in collaboration with Privacy International.
On October 17th 2019, the UN Special Rapporteur (UNSR) on Extreme Poverty and Human Rights, Philip Alston, released his thematic report on digital technology, social protection and human rights. Understanding the impact of technology on the provision of social protection – and, by extent, its…
Content type: Press release
Tomorrow, the UN Special Rapporteur on extreme poverty and human rights will present his annual report to the UN General Assembly in New York on digital technology, social protection and human rights. On the same day, Privacy International will be launching its own series on surveillance in the provision of social services.
The Special Rapporteur warns that specific areas need to be addressed to "avoid stumbling zombie-like into a digital welfare dystopia" and that "values such as…
Content type: Long Read
This research is the result of a collaboration between Grace Tillyard, a doctoral researcher in the Media, Communications and Cultural Studies department at Goldsmiths College, London, and Privacy International.
Social Protection Systems in the Digital Age
In the digital age, governments across the world are building technologically integrated programmes to allow citizens to access welfare payments. While smart and digital technologies hold the potential to streamline administrative…
Content type: News & Analysis
Photo by VanveenJF on Unsplash
Last week, Amnesty International published a report revealing the Moroccan government appears to have been using spyware from Israeli company NSO Group against two human rights defenders, historian and columnist Maati Monjib and lawyer Abdessadak El Bouchattaoui.
In order for the government to gain control over their phones, Monjib and El Bouchattaoui had to click on a malicious link which would install NSO Group’s Pegasus spyware. NSO therefore has to craft…
Content type: Long Read
[Photo credit: Images Money]
The global counter-terrorism agenda is driven by a group of powerful governments and industry with a vested political and economic interest in pushing for security solutions that increasingly rely on surveillance technologies at the expenses of human rights.
To facilitate the adoption of these measures, a plethora of bodies, groups and networks of governments and other interested private stakeholders develop norms, standards and ‘good practices’ which often end up…
Content type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content type: News & Analysis
On 11 October 2019, Privacy International together with EDRi, BEUC, AccessNow and Open Society European Policy Institute, sent an open letter to EU Member States, to urge them to conclude the negotiations on the ePrivacy Regulation.
The letter highlights the urgent need for a strong ePrivacy Regulation in order to tackle the problems created by the commercial surveillance business models, and expresses the deep concerns by the fact that the Member States, represented in the Council of the…
Content type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content type: News & Analysis
The latest news of Twitter “inadvertently” sharing email addresses or phone numbers provided for safety or security purposes (for example, two-factor authentication) for advertising purposes is extremely concerning for several reasons.
First of all, it is not the first time for Twitter's used people's data in ways they wouldn't expect or that ignores their choices: in August, the company disclosed that it may have shared data on users with advertising partners, even if they had opted out from…
Content type: News & Analysis
Photo by Daniel Jensen on Unsplash
Everyone is talking about Facebook's end-to-end encryption plans and the US, UK and Australian government's response. Feeling lost? Here is what you need to know.
What's Facebook trying to do?
First let's be clear: Facebook has many faults when it comes to privacy. It's also suffered a number of security failures recently. See here for instance.
In response to their successive failures to protect your privacy, Facebook announced in their 'pivot to privacy…
Content type: News & Analysis
Today’s announcement regarding the UK and US agreement signed pursuant to the US CLOUD Act is being touted on both sides of the Atlantic as a major victory for law enforcement and security. But it is a step backward for privacy.
And it’s far more complicated than their press release and letter to industry.
The agreement replaces the prior system, under which law enforcement agencies from around the world, including the UK, had to meet US legal standards in order to get access to content held…
Content type: Long Read
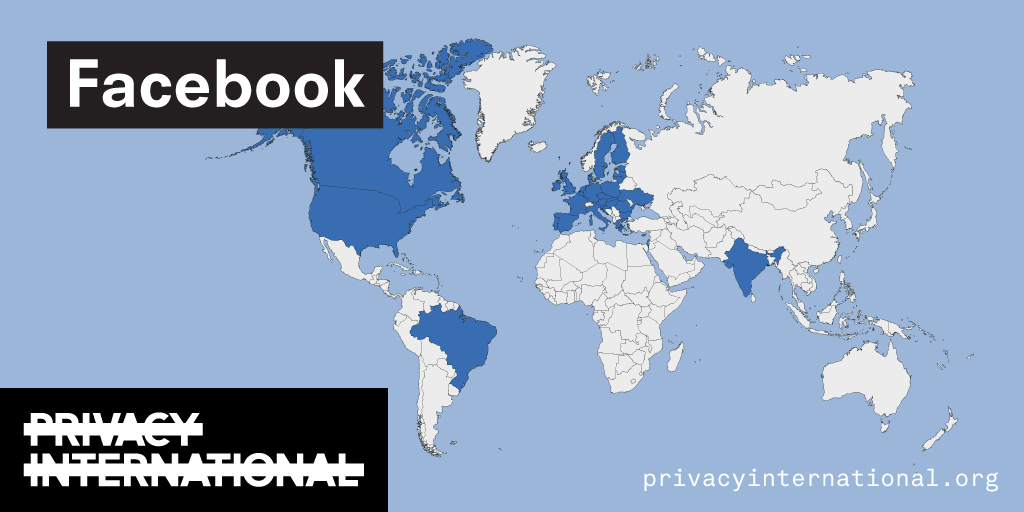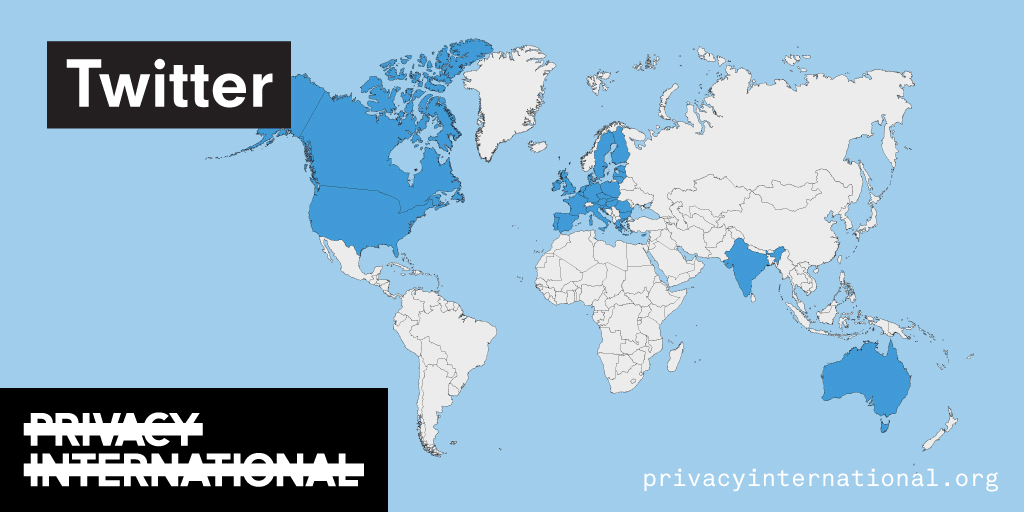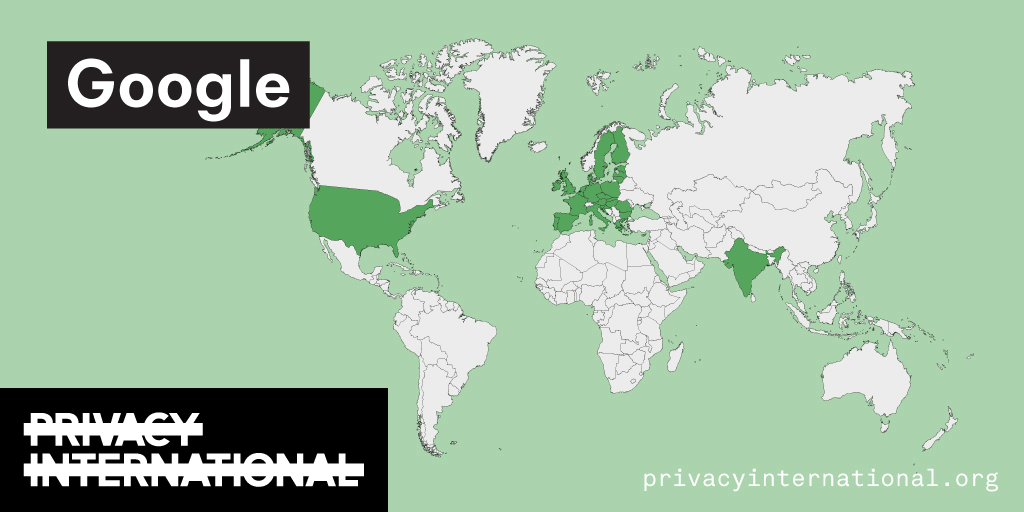
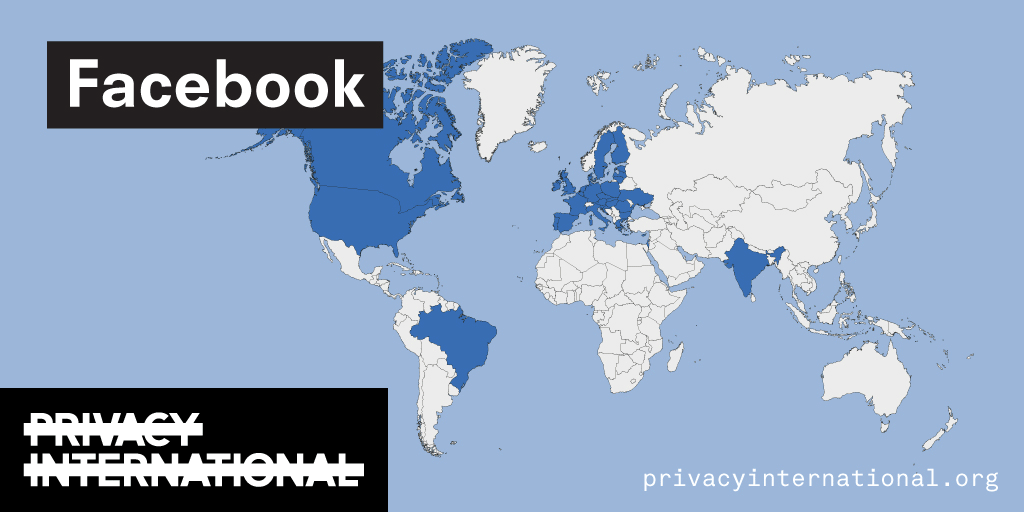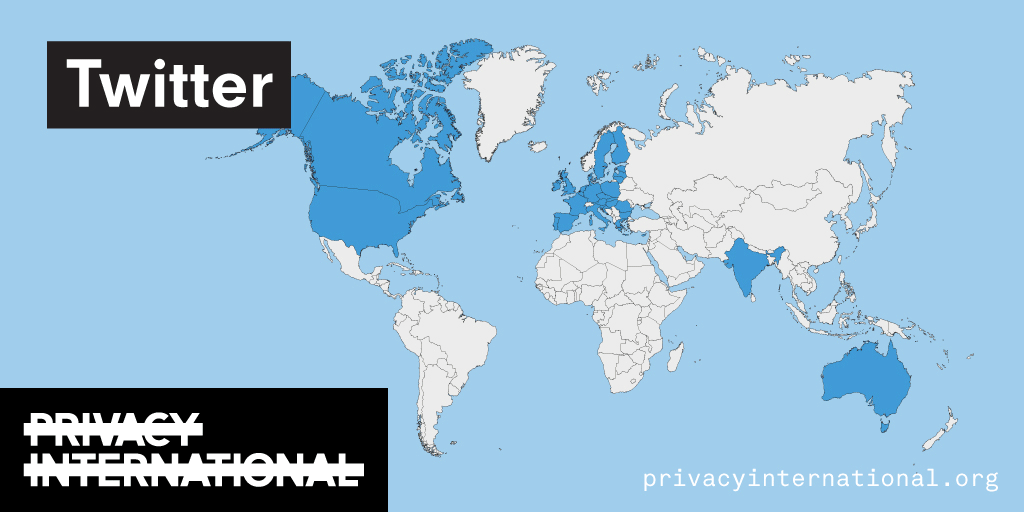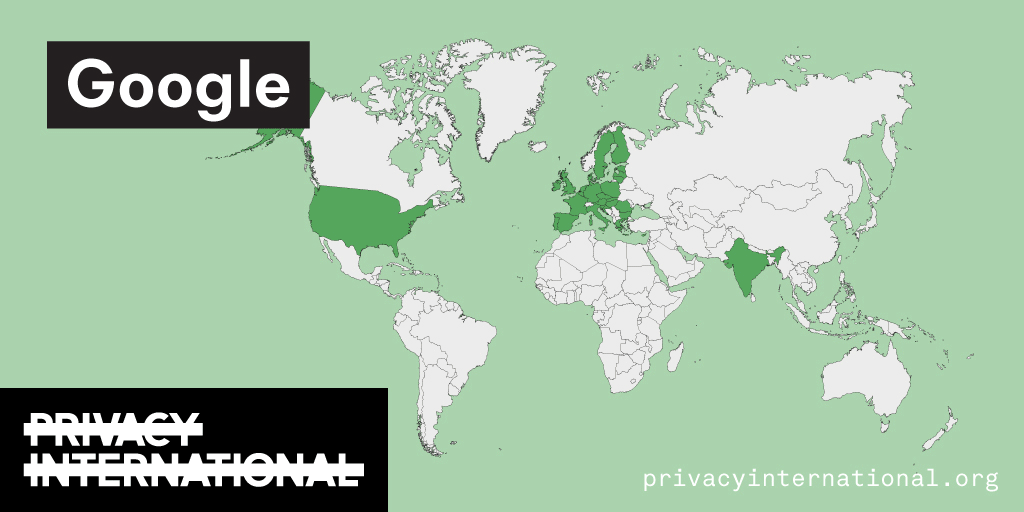
An analysis of what Facebook, Google, and Twitter have done to provide users with political ad transparency as of September 2019. Our full analysis is linked below.
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign entities, and more. Significant…
Content type: News & Analysis
A new UK Times report claims that “WhatsApp, Facebook and other social media platforms will be forced to disclose encrypted messages from suspected terrorists, paedophiles and other serious criminals under a new treaty between the UK and the US.”
Several other media outlets have followed up on the report, with headlines such as “UK and US set to sign treaty allowing UK police ‘back door’ access to WhatsApp and other ‘end to end encrypted’ messaging platforms”.
While the…
Content type: News & Analysis
Photo: The European Union
“Border Externalisation”, the transfer of border controls to foreign countries, has in the last few years become the main instrument through which the European Union seeks to stop migratory flows to Europe. Similar to the strategy being implemented under Trump’s administration, it relies on utilising modern technology, training, and equipping authorities in third countries to export the border far beyond its shores.
It is enabled by the adoption…
Content type: News & Analysis
Photo by Francesco Bellina
The wars on terror and migration have seen international funders sponsoring numerous border control missions across the Sahel region of Africa. Many of these rely on funds supposed to be reserved for development aid and lack vital transparency safeguards. In the first of a series, freelance journalist Giacomo Zandonini sets the scene from Niger.
Surrounded by a straw-yellow stretch of sand, the immense base of the border control mobile company of Maradi, in southern…
Content type: Long Read
Photo: Francesco Bellina
Driven by the need to never again allow organised mass murder of the type inflicted during the Second World War, the European Union has brought its citizens unprecedented levels of peace underpinned by fundamental rights and freedoms.
It plays an instrumental role in protecting people’s privacy around the world; its data protection regulation sets the bar globally, while its courts have been at the forefront of challenges to unlawful government surveillance…
Content type: News & Analysis
Today, the High Court of South Africa in Pretoria in a historic decision declared that bulk interception by the South African National Communications Centre is unlawful and invalid.
The judgment is a powerful rejection of years of secret and unchecked surveillance by South African authorities against millions of people - irrespective of whether they reside in South Africa.
The case was brought by two applicants, the amaBhungane Centre for Investigative Journalism and journalist Stephen…