Advanced Search
Content Type: Explainer
La ‘Guía para protegerte digiralmente durante una protesta' es un documento enfocado en Colombia que recopila información básica sobre las capacidades de vigilancia que posee la policía colombiana, y mejores prácticas para evitarla. Encontrarás en esta guía definiciones, explicaciones y recomendaciones sobre la vigilancia a los dispositivos tecnológicos, las comunicaciones, la identidad y las redes sociales de las personas que protestan.
Puedes descargar la guía desde esta página, de la…
Content Type: Explainer
The ‘Guide to Digital Safety and Privacy at Peaceful Protests’ has been produced by 7amleh - The Arab Center for the Advancement of Social Media.
7amleh has adapted the content of PI's UK Free to Protest guide to fit the Palestinian context. The guide is organized in three sub-guides: (1) a guide to digital safety and privacy at peaceful protests; (2) a guide to surveillance of protesters’ faces and bodies; and (3) a guide to policing databases and predictive policing tools.
This guide was…
Content Type: Explainer
La 'Guía de Protesta' es un documento que buscar concientizar sobre las herramientas tecnológicas que las fuerzas de seguridad podrían utilizar para monitorear e identificar personas en una protesta en Argentina. Encontrarás en esta guía explicaciones de cómo las tecnologías de vigilancia están siendo utilizadas para vigilar las protestas, y cómo puedes protegerte de las mismas.
Puedes descargar la guía desde esta página, de la sección más abajo titulada "Attachments".
This guide was…
Content Type: Press release
Today, the High Court ruled that the Home Secretary acted unlawfully and breached human rights and data protection laws by operating a secret, blanket policy of seizing, retaining and extracting data from the mobile phones of asylum seekers arriving by small boat.
This claim for judicial review was brought by three asylum seeking claimants: HM represented by Gold Jennings, and KA and MH represented by Deighton Pierce Glynn. The Claimants, like thousands of others arriving by small boat, all…
Content Type: News & Analysis
Background
Today judgment has been handed down in the landmark case of R (HM and MA and KH) v Secretary of State for the Home Department.
This is a Judicial Review decision concerning the UK Home Office’s secret and blanket policy of seizing mobile phones of all migrants who arrived to the UK by small boat between April 2020 and November 2020, and extracting data from all phones. PI was a third party intervener in the case.
The case revealed that migrants were searched on arrival at Tug Haven…
Content Type: Long Read
In a roundtable available on YouTube, co-hosted with Garden Court Chambers, Privacy International brought together immigration law practitioners to discuss how they’ve used privacy and data protection law to seek information or redress for their clients.Index:1. UK Border 20252. Super-complaint and judicial review challenge to data sharing3. Mobile phone seizure and extraction4. Freedom of Information Act requestsThe dystopian future: UK Border 2025To set the scene on how the future may look…
Content Type: Examples
Clashes between police and lockdown protesters have spawned reports of police brutality in Greece. Mobile phone footage of one such protest in March 2021 suggested that the police are using drones to surveil the protests, and some of those remanded have complained that they’ve been beaten and subjected to threats and sexual harassment while in custody. Disinfaux Collective has identified an individual caught on video throwing a petrol bomb as “either a police officer of the DRASI unit… or,under…
Content Type: News & Analysis
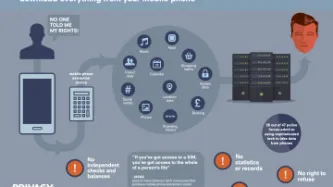
Around the world, we see migration authorities use technology to analyse the devices of asylum seekers. The UK via the Policing Bill includes immigration officers amongst those who can exercise powers to extract information from electronic devices. There are two overarching reasons why this is problematic:
The sole provision in the Policing Bill to extract information rests on voluntary provision and agreement, which fails to account for the power imbalance between individual and state. This…
Content Type: News & Analysis
It is difficult to imagine a more intrusive invasion of privacy than the search of a personal or home computer ... when connected to the internet, computers serve as portals to an almost infinite amount of information that is shared between different users and is stored almost anywhere in the world.
R v Vu 2013 SCC 60, [2013] 3 SCR 657 at [40] and [41].
The controversial Police Crime Sentencing and Courts Bill includes provision for extracting data from electronic devices.
The Bill…
Content Type: Explainer
‘Free to Protest: The protestor’s guide to police surveillance and how to avoid it’ (UK edition) is a collection of bite-sized guides about high-tech police surveillance capabilities at protests, including tips and strategies about how you can protect yourself from being identified, tracked and monitored. Each guide is self-contained so you don’t need to read the whole thing, or read it any particular order. You can access each separate section of the guide from the campaign homepage, but if…
Content Type: Explainer
What are ‘cloud extraction tools’ and what do they do?
Cloud extraction technology enables the police to access data stored in your ‘Cloud’ via your mobile phone or other devices.
The use of cloud extraction tools means the police can access data that you store online. Examples of apps that store data in the Cloud include Slack, Instagram, Telegram, Twitter, Facebook and Uber.
How might cloud extraction tools be used at a protest?
In order to extract your cloud data, the police would…
Content Type: Explainer
What do mobile phone extraction tools do?
Mobile phone extraction (MPE) tools are devices that allow the police to extract data from mobile phones, including:
contacts;
call data (i.e. who you call, when, and for how long);
text messages (including who you texted and when);
stored files (photos, videos, audio files, documents etc);
app data (including the data stored on these apps);
location information history;
wifi network connections (which can reveal the locations of any…
Content Type: News & Analysis
The Police, Crime, Sentencing and Courts (PCSC) Bill is currently being scrutinised by numerous civil society organisations such as Amnesty International UK and Liberty for its damaging impacts on peaceful protests, however it also contains important provisions regarding when, if and how the police and other governmental authorities can extract data from your phones and other electronic devices.
Chapter 3 of the PCSC Bill is a legislative response to the UK's Information Commissioner's Office…
Content Type: Long Read
There are few places in the world where an individual is as vulnerable as at the border of a foreign country.As migration continues to be high on the social and political agenda, Western countries are increasingly adopting an approach that criminalises people at the border. Asylum seekers are often targeted with intrusive surveillance technologies and afforded only limited rights (including in relation to data protection), often having the effect of being treated as “guilty until proven…
Content Type: Report
In December 2019 Privacy International made submissions to Police Scotland in relation to documents designed to explain to the public how cyber kiosks will work and what information will be given to victims when Police Scotland extract data from their phone.
Police Scotland rely on 'consent' to seize a phone from a victim. We believe the lack of information provided to the individual regarding extraction, examination, retention, deletion, sharing and search parameters undermines that any…
Content Type: Video
You’re a witness or a victim or a suspect of a crime; or even just travelling going on holiday. Officials demand your phone, then disappear with it. What happened to your phone? What happened to your data? What will happen to you?
We all generate vast amounts of data using our mobile phones - more than most of us are aware of - and that data has become increasingly attractive to law enforcement agencies around the world, enabled by ‘extraction technologies’ supplied by companies like…
Content Type: Case Study
Anyone who is arrested should be informed of the reasons for their arrest and any charges against them. Anyone who is detained is also entitled to a trial within a reasonable time, or to be released if no charges are held against them.
Privacy enhances these protections. It provides limitations on the manner in which information can be obtained about you, and the kind of information that can be accessed about you by law enforcement, who can access that information and how they can use it.…
Content Type: Advocacy
In December 2019 Privacy International made submissions to Police Scotland in relation to documents designed to explain to the public how cyber kiosks will work and what information will be given to victims when Police Scotland extract data from their phone.
Police Scotland rely on 'consent' to seize a phone from a victim. We believe the lack of information provided to the individual regarding extraction, examination, retention, deletion, sharing and search parameters undermines that any…
Content Type: Press release
Following Police Scotland’s announcement that they will be rolling out cyber kiosks to police stations across Scotland. Open Rights Group and Privacy International have released a statement:
Open Rights Group and Privacy International called on Police Scotland to prevent rolling out until the Scottish Government reformed the law to provide an overarching framework for the seizure of electronic devices in Scotland in line with human rights standards. That recommendation has not been heeded by…
Content Type: News & Analysis
In the last few months strong concerns have been raised in the UK about how police use of mobile phone extraction dissuades rape survivors from handing over their devices: according to a Cabinet Office report leaked to the Guardian, almost half of rape victims are dropping out of investigations even when a suspect has been identified. The length of time it takes to conduct extractions (with victims paying bills whilst the phone is with the police) and the volume of data obtained by the…
Content Type: Long Read
In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone…
Content Type: Report
“...a mobile device is now a huge repository of sensitive data, which could provide a wealth of information about its owner. This has in turn led to the evolution of mobile device forensics, a branch of digital forensics, which deals with retrieving data from a mobile device.”
The situation in Scotland regarding the use of mobile phone extraction has come a long way since the secret trials were exposed. The inquiry by the Justice Sub-Committee, commenced on 10 May 2018, has brought much…
Content Type: Explainer
We look at the recently published report on forensic science in the UK, highlight concerns about police not understanding new tech used to extract data from mobile phones; the risk of making incorrect inferences and the general lack of understanding about the capabilities of these tools.
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. So starts the damning report of the House of Lords Science and Technology Select…
Content Type: News & Analysis
It's a big question, have you purchased a card for your local surveillance camera on Surveillance Camera Day?
Yes, Surveillance Camera Day is a real thing and happens on 20 June.
Perhaps your local community could create a bingo card to see who knows where all the local cameras are. Are there any on your local bins, how about the lampposts or a billboard?
Have you had a facial recognition van in your local community? Did you see the police helicopter crew video camera…
Content Type: News & Analysis
We look at the recently published report on forensic science in the UK, highlight concerns about police not understanding new tech used to extract data from mobile phones; the risk of making incorrect inferences and the general lack of understanding about the capabilities of these tools.
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. So starts the damning report of the House of Lords Science and Technology Select…
Content Type: News & Analysis
A mobile device is a huge repository of sensitive data, which could provide a wealth of information about its owner and many others with whom the user interacts.
Companies like Cellebrite, MSAB and Oxygen Forensics sell software and hardware to law enforcement. Once your phone is connected to one of these mobile phone extraction tools, the device extracts, analyses and presents the data contained on the phone.
What data these tools can extract and what method is used will…
Content Type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content Type: Press release
Creative Commons Photo Credit: Source
Have the police been unlawfully hacking our phones? Privacy International refers this question to Lord Justice Sir Adrian Fulford, the Investigatory Powers Commissioner
Privacy International has formally written to the UK's Investigatory Powers Commissioner about the police's use of intrusive 'mobile phone extraction' (MPE) technology, raising concerns about whether in some, or indeed in all circumstances, its use constitutes either an interception…
Content Type: News & Analysis
Following on from the publication of our ‘Digital Stop and Search’ report last month, into the use of intrusive technology that enables officers to download all of the data stored on our mobile phones, we are pleased that Scotland's Justice Sub-Committee on Policing have been scrutinising Police Scotland over their use of the technology.
During the hearing by Scotland's Justice Sub-Committee on Policing on 10th May John Finnie MSP stated he personally did not feel reassured, after grilling…