Advanced Search
Content Type: Long Read
As our four year battle against the UK government’s extraordinarily broad and intrusive hacking powers goes to the Supreme Court, we are launching a new fundraising appeal in partnership with CrowdJustice.
We are seeking to raise £5k towards our costs and need your help. If we lose, the court may order us to pay for the government’s very expensive army of lawyers. Any donation you make, large or small, will help us both pursue this important case and protect the future ability of…
Content Type: Report
In December 2018, the National Coalition of Human Rights Defenders-Kenya published a report analysing the needs and concerns of human rights defenders (HRD) in relation to privacy, data protection and communications surveillance.
A summary of their findings is below. Access the full report on their website.
Content Type: Long Read
It’s 15:10 pm on April 18, 2018. I’m in the Privacy International office, reading a news story on the use of facial recognition in Thailand. On April 20, at 21:10, I clicked on a CNN Money Exclusive on my phone. At 11:45 on May 11, 2018, I read a story on USA Today about Facebook knowing when teen users are feeling insecure.
How do I know all of this? Because I asked an advertising company called Quantcast for all of the data they have about me.
Most people will have never heard of…
Content Type: Long Read
Photo Credit: Max Pixel
The fintech sector, with its data-intensive approach to financial services, faces a looming problem. Scandals such as Cambridge Analytica have brought public awareness about abuses involving the use of personal data from Facebook and other sources. Many of these are the same data sets that the fintech sector uses. With the growth of the fintech industry, and its increase in power and influence, it becomes essential to interrogate this use of data by the…
Content Type: Long Read
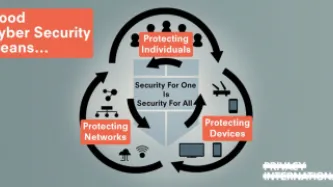
Since 2004, October has been designated National Cyber Security Awareness Month in the United States. Many other countries have followed suit, as part of the effort to raise awareness about the importance of cybersecurity, and how we can all work together to improve it.
However, cyber security (or sometimes, just ‘cyber’) has not only become a term with multiple and sometimes contradictory meanings - that go from digital security or digital diplomacy to criminal activities with a digital…
Content Type: Long Read
Photo credit: Pixabay
This piece was originally published in iNews
It seems that you can’t go anywhere online at the moment without being reassured that ‘we respect your privacy’ and being directed to a 2,000-word privacy policy. You probably just click ‘got it, thanks’ because who has the luxury to stop and think about what their ‘privacy’ actually means?
But privacy is something that starts becoming far less abstract when you can see how it is being threatened and undermined, every day and…
Content Type: Long Read
This piece was originally published in Just Security.
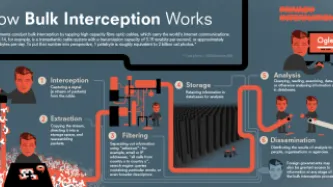
Earlier this month, the European Court of Human Rights issued a major judgment in three consolidated cases challenging the U.K. government’s mass interception program, which was first revealed by Edward Snowden in 2013. That judgment finds notable deficiencies in the legal framework governing mass interception, rendering the program unlawful under Articles 8 and 10 of the European Convention on Human Rights (ECHR), which protect the rights…
Content Type: Long Read
Written jointly by Privacy International and the American Civil Liberties Union (ACLU).
In a landmark decision earlier this month, the European Court of Human Rights ruled that one of the mass surveillance programs revealed by Edward Snowden violates the rights to privacy and freedom of expression. While the case challenges the U.K. government’s mass interception of internet traffic transiting its borders, the court’s judgment has broader implications for mass spying programs in Europe and…
Content Type: Long Read
Image attribution: By Legaleagle86 at en.wikipedia, CC BY-SA 3.0.
In a long-anticipated judgment, the Indian Supreme Court has ruled that India's controversial identification system Aadhaar is Constitutional. They based their conclusion on notes that there are sufficient measures in place to protect data, and that it is difficult to undertake surveillance of citizens on the basis of Aadhaar.
But there is some good in this ruling. The court has demanded that the Government introduce…
Content Type: Long Read
The UK's domestic-facing intelligence agency, MI5, today admitted that it captured and read Privacy International's private data as part of its Bulk Communications Data (BCD) and Bulk Personal Datasets (BPD) programmes, which hoover up massive amounts of the public's data. In further startling legal disclosures, all three of the UK's primary intelligence agencies - GCHQ, MI5, and MI6 - also admitted that they unlawfully gathered data about Privacy International or its staff. You can read the…
Content Type: Long Read
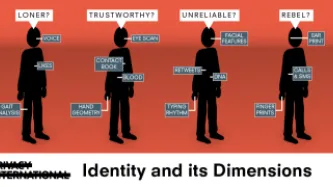
Who are you? The Challenges of Identity and Identification
“Identity” is a word that covers an incredible range of contested, deeply personal and highly politicised questions. These range from the political and the sociological, through to the psychological and philosophical. A question such as “who are you?” can elicit a multiplicity of responses, none of which are straightforward, are sometimes highly contextual, and are often deeply contested.
However, there is something of an attempt to…
Content Type: Long Read
The European Court of Human Rights ruled today that the UK government's mass interception program violates the rights to privacy and freedom of expression. The Court held that the program "is incapable of keeping the 'interference' to what is 'necessary in a democratic society'". This finding is an important victory for human rights and the rule of law. Below, we break down the key parts of the decision.
The Court's ruling comes after a five-year battle against two UK mass surveillance…
Content Type: Report
Intelligence sharing between countries is one of the most pervasive and least regulated surveillance practices carried out by governments across the world. It is facilitated by rapidly evolving surveillance technologies that enable intelligence agencies to collect, store, analyse and share ever larger amounts of people’s personal information.
This briefing paper, written jointly by the International Network of Civil Liberties Organizations (INCLO) and PI, sets out urgent recommendations that…
Content Type: Long Read
National and International civil society organisations (CSOs) play vital roles in many aspects of our societies as watchdogs of state powers, as representatives of the voices of the people, as experts to inform and educate an array of stakeholders.
One of our key lessons learned from three decades of work, including 10 years with the Privacy International Networkto build a global privacy movement,promoting and advocating for the highest privacy and data protection safeguards has been…
Content Type: Report
Esta parte de "Las Claves para Mejorar la Protección de Datos" proporciona enlaces a recursos adicionales y describe las vías de participación para mejorar el involucramiento de las organizaciones de la sociedad civil en estos temas.
Content Type: Report
This part of “The Keys to Data Protection” outlines the models and structures as well as powers and functions of an independent supervisory authority, which plays an essential role as an independent oversight and enforcement mechanism of data protection law.
Content Type: Report
Esta parte de "Las Claves para Mejorar la Protección de Datos" presenta las responsabilidades, obligaciones y responsabilidades de quienes procesan datos personales, para garantizar que sean responsables ante la ley.
Content Type: Report
This part of “The Keys to Data Protection” outlines and explains the legal basis permitted for the processing of personal data, which should be limited and clearly articulated in law.
Content Type: Report
Esta parte de "Las Claves para Mejorar la Protección de Datos" presenta los derechos clave para los titulares de protección de datos personales, que deben ser respetados y aplicados por quienes procesan efectúan tratamiento de datos.
Content Type: Report
Esta parte de "Las Claves para Mejorar la Protección de Datos" presenta disposiciones generales para una ley de protección de datos, que incluyen el objeto y el propósito de la ley y las definiciones básicas que debe contener.
Content Type: Report
This part of “The Keys to Data Protection” presents and explains seven key data protection principles, derived from regional and international frameworks, covering elements such as minimisation, storage limitation, and accountability.
Content Type: Report
This part of “The Keys to Data Protection” explains what data protection is, why it is needed, and how to works. It also outlines why it is essential for the exercise of the right to privacy. This part also provides a brief outline of data protection in practice.
Content Type: Long Read
The Sustainable Development Goals (SDGs) are the United Nations-led initiative to define the development agenda. Building on the eight Millennium Development Goals, the SDG’s 17 goals – and the 169 targets – serve as an opportunity to tackle many of the most pressing issues in the world today. The SDGs are also explicitly grounded in human rights. Goal 16 on “peace, justice, and sustainable institutions” aims to “Promote peaceful and inclusive societies for sustainable development, provide…
Content Type: Long Read
Privacy International’s new report shows how countries with powerful security agencies are training, equipping, and directly financing foreign surveillance agencies. Driven by advances in technology, increased surveillance is both powered by and empowering rising authoritarianism globally, as well as attacks on democracy, peoples’ rights, and the rule of law.To ensure that surveillance powers used by governments are used to protect rather than endanger people, it is essential that the public,…
Content Type: Long Read
The idea of a “smart city” is primarily a marketing concept, used to sell data-intensive technologies under the pretext of improving the functioning of cities. This could include injecting ‘smart’ tech into delivering services, public safety, environmental monitoring, traffic control, among other possible applications.
One in particular aspect of smart cities has been consistently problematic: how these projects are used to boost law enforcement and policing under the guise of public safety.…
Content Type: Long Read
Creative Commons Photo Credit: Source
UPDATE: 30 July 2019
Privacy International has identified the following:
Two RAB officers received approval to travel to the USA in April 2019 for training on “Location Based Social Network Monitoring System Software for RAB Intelligence Wing”
Three RAB officers received approval to travel to Russia in August 2017 to participate in user training of “Backpack IMSI Catcher (2G, 3G, 4G)” paid for by Annex SW Engineering, a…
Content Type: Long Read
Creative Commons Photo Credit: Source
In the midst of continued widespread public outrage at the US government’s brutal ‘zero-tolerance’ policy around immigration – multiple data and analytics companies have quietly avoided answering questions about their role in feeding the US Immigration and Customs Enforcement (ICE) agency’s data backbone. These companies are bidding to work with an agency that has time and time again shown itself to be a brutal and problematic.
Privacy International…
Content Type: Report
The Information Commissioner’s Office (ICO) recently issued a series of decisions in Privacy International’s long-running battle for information about UK police forces' acquisition of IMSI catchers. This case study provides an in-depth summary and analysis of this process.
We hope it is useful to both campaigners seeking greater transparency from policing bodies, and more widely to Freedom of Information campaigners who are trying to challenge 'neither confirm nor deny' responses to FOI…