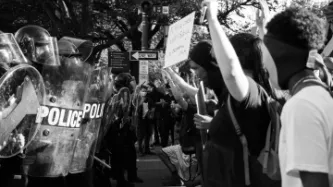Search
Content type: Examples
Italy has launched Immuni, one of the first contact tracing apps based on the Apple-Google API. The app is opt-in, and includes an explanation of the privacy and security measures in its setup. The app collects anonymously bluetooth tokens that are automatically randomised, but does not collect GPS or location data and performs all processing on the device.
Source: https://9to5mac.com/2020/06/01/italy-apple-exposure-notification-api-app/
Writer: Michael Potuck
Publication: 9 to 5 Mac
Content type: News & Analysis
For the past few weeks, people across the world, starting in the US, have taken to the streets to protest the murder of George Floyd, a victim of police brutality. The protests, which are organised by and in support of the Black Lives Matter movement have also become a platform to protest against state sponsored violence and systematic racism against black people.
The majority of articles and media focus have so far focused on what happens during the protest, namely an increasingly militarised…
Content type: Long Read
In December 2019, the Information Rights Tribunal issued two disappointing decisions refusing appeals brought by Privacy International (PI) against the UK Information Commissioner.
The appeals related to decisions by the Information Commissioner (IC), who is responsible for the UK’s Freedom of Information regime, concerning responses by the Police and Crime Commissioner for Warwickshire and the Commissioner of Police for the Metropolis (The Metropolitan Police) to PI’s freedom of information…
Content type: Examples
Serbian MPs voted 155-0, with one not voting and one abstention, to lift the state of emergency that was declared on March 15 and repeal 11 emergency ordinances covering work, tax, debt, and criminal justice on the basis that the conditions for lifting it have been met. The change lifts curfews and allows businesses to reopen, but sanitary and medical measures to control the coronavirus pandemic remain in force, such as the requirement to maintain social distancing in shopping malls, cafes, and…
Content type: Examples
The Slovak Constitutional Court declared unconstitutional parts of the newly amended telecommunication law that permitted state authorities to access telcommunications data for the purposes of contact tracing. The parliament approved the legislation in March, but the court ruled that the need for speedy solutions during the pandemic should not unintentionally erode the rule of law. The court called the provisions it struck down insufficiently clear, and lacking in safeguards against misuse. The…
Content type: Examples
As part of their preparations to ease the lockdown, French authorities have added AI tools into the CCTV cameras in the Paris Metro to detect the number of passengers who are wearing face masks. The system is also being used in outdoor markets and buses in Cannes. Although it is mandatory to wear a mask on public transport in France, the software won't be used to identify, rebuke, or fine people, and the system has not proved as contentious as contact tracing. The data protection regulator CNIL…
Content type: Examples
Taking advantage of the pandemic to close US borders, the Trump administration is also spreading coronavirus infection by deporting detainees to receiving countries such as Guatemala, where 20% of infections are deportees. Guatemala has only two hospitals and a scattering of smaller regional medical facilities to serve its population of 18 million people. As of April 2020, 5,000 Guatemalans were being held in detention in the US, and every week the Department of Homeland Security was sending…
Content type: Examples
The controversial Israeli spyware company NSO Group's US arm, Westbridge, has been trying to pitch its phone hacking software to US law enforcement agencies such as the San Diego Police Department, particularly a tool called "Phantom", which the complany claims can overcome encryption, track geolocation, withstand a factory reset, monitor apps and voice and VOIP calls, and collect passwords.
Writer: Joseph Cox
Publication: Vice
Content type: Examples
Cameras repurposed as "fever-detecting" aren't designed for and are not very good at detecting infections, but businesses, airlines, major employers, and public officials are nonetheless reacting to the coronavirus pandemic by spending large sums to buy them without understanding their limitations. The systems can detect elevated skin temperatures, but aren't precise enough to be able to identify the cause. In addition, many people who develop COVID-19 don't have fevers. The scanners have not…
Content type: Examples
At a press conference, Israeli prime minister Benjamin Netanyahu suggested that microchipping everyone, beginning with children returning to school and kindergarten as the coronavirus lockdown ends; the chip would sound an alarm whenever anyone gets too close much as a car does. Security experts immediately objected on the grounds that microchipping kids was neither legal nor practical, that the children would be at risk from paedophiles if their data leaked to the internet; and that the real…
Content type: Examples
Any user of India's Aaorgya Setu contact tracing app can now request deletion of the data they've entered according to the Aaorgya Seta Emergency Data Access and Knowledge Sharing Protocol, 2020, which specifies the definition, collection, processing, and storage of the data the app collects. The protocol will be applicable for the next six months, and also increases the amount of time the data will be retained from 60 days to 180. IT ministry officials said the protocol was needed after a…
Content type: Examples
Many of the technologies used to combat the coronavirus pandemic, including monitoring and analysing social media posts, telecommunications location data, and the use of sensors, were first tested on refugees during the 2015 crisis and are now being repurposed in the name of public health. In 2019, the European border security agency Frontex published a €400,000 tender for social media analysis services hoping to better predict future migration patterns; the tender was withdrawn after an…
Content type: Examples
Among the regulations governing restaurants as the US State of Maine's moves into a phased reopening is a requirement to maintain customer records for contact tracing purposes, including one customer's name and contact information per party and those of the table's server. The regulations also recommend promoting contactless payment options.
Writer: State of Maine
Publication: State of Maine
Content type: Examples
In designing its Healthy Together contact tracing app, the US state of Utah opted for a GPS and Bluetooth-based design created by social media startup Twenty; it does not use the Google-Apple API. The goal is for the app to assist the 1,200 Utah Department of Health workers who are doing phone call-based contact tracing. Twenty believes the app's ability to store location and contact history over 14 days can cut the length of phone calls from one hour to 16 minutes. The Apple-Google platform…
Content type: Examples
In its final report, the expert group appointed by the Norwegian Ministry of Health and Care Services to assess the security and privacy of the country's COVID-19 contact tracing app, "Smittestopp", concluded that the app handles neither responsibly. The group recommended removing all data once it's not needed (15 to 16 days for location data, for example), implement differential privacy, open the source code wherever possible, and regularly reevaluate the app against its two purposes: contact…
Content type: Examples
France, like the UK, opted to develop its own contact tracing app. "StopCovid", using a centralised design developed by the Pan-European Privacy-Preserving Proxity Tracing (PEPP-PT) group, which created a framework called ROBust and the privacy-presERving proximity Tracing protocol (ROBERT). French ministers have defended the decision to choose ROBERT rather than the decentralised options, DP3T or Apple's and Google's jointly developed API, saying that the app is not intended to monitor…
Content type: Examples
As the waning pandemic leads to signs that the protest movement is resuming, China is moving to draft new national security legislation and incorporate it into Hong Kong's Basic Law, bypassing the territory's Legislative Council. Elections for the Council are due to be held in September, and Chinese officials are concerned that they could lose its pro-Beijing majority. Under Article 23 of the Basic Law, Hong Kong's government and legislature were required to enact and pass national security…
Content type: Examples
INTERNETLAB offers an extensive analysis of all the eight different Covid-19 related apps being discussed in Brazil at the moment. Apps were rated according to four parameters: consent, need, transparency and security. Besides this, the organisation takes a look into what permissions which app has and analyses these permissions in light of what the apps promise to deliver.
Writer: Alessandra Gomes, Maria Luciano, Nathalie Fragoso e Victor Pavarin
Publication: INTERNETLAB
…
Content type: Examples
Following a similar effort in the Netherlands, the UK is planning a national research programme in collaboration with universities, water companies, and public research bodies to detect coronavirus in sewage for use as an early warning system for future outbreaks of COVID-19. About half of those infected with SARS-CoV-2 excrete it in feces, and enough survives when sewage reaches treatment plants to test successfully for its genetic fingerprint using PCR analysis. The Dutch programme is run by…
Content type: Examples
Immunity passports are likely to increase discrimination and threaten fairness and public health - and won't work for practical reasons. First and foremost, scientists do not yet know whether infection confers immunity or for how long; the serological tests so far developed are insufficiently reliable; the volume of testing required is not feasible; and no country has enough survivors of COVID-19 to boost its economy. There are also numerous ethical objections.
Writer: Natalie Kofler and…
Content type: Examples
It's been two months since the launch of "Perú en us manos", the mobile app promoted by the Peruvian government amidst the Covid-19 pandemic. Until now the app did not accomplish the ambitious goals it set out to.
On its first month the app had detected 1400 risk zones while there where already 36,000 confirmed infection cases. There is little transparency on how those risk zones are estimated. Developers of the app state that only one fifth of the data provided by the Health Ministry is clean…
Content type: Video
You can find out more about Haki na Sheria here: http://hakinasheria.org/
Find out more about double registration in Keren's piece "In Kenya, thousands left in limbo without ID cards" in CodaStory: https://www.codastory.com/authoritarian-tech/kenya-biometrics-double-registration/
Find out more about the Huduma Namba case on our website: https://privacyinternational.org/news-analysis/3350/why-huduma-namba-ruling-matters-future-digital-id-and-not-just-kenya
You can listen and…
Content type: People
Ksenia is a Legal Officer at PI. She leads PI’s programme focusing on police surveillance technologies, data exploitation and the law. She is also responsible for legal research and litigation on surveillance and data protection. Prior to joining PI, Ksenia taught law at Queen Mary, University of London and Royal Holloway, University of London.
Ksenia has a PhD from Queen Mary, University of London. Her research examined the contemporary phenomenon of ‘revenge pornography’ and analysed…
Content type: News & Analysis
On June 9th, in light of the global debate against racial injustices, the company IBM announced they would stop selling facial recognition. In a letter to the US congress, they demanded a “national dialogue on whether and how facial recognition technology should be employed by domestic law enforcement agencies.”
It is worth noting first of all that it is not entirely clear that IBM is actually stopping facial recognition. The letter states that "IBM no longer offers general purpose IBM facial…
Content type: News & Analysis
Yesterday, Amazon announced that they will be putting a one-year suspension on sales of its facial recognition software Rekognition to law enforcement. While Amazon’s move should be welcomed as a step towards sanctioning company opportunism at the expense of our fundamental freedoms, there is still a lot to be done.
The announcement speaks of just a one-year ban. What is Amazon exactly expecting to change within that one year? Is one year enough to make the technology to not discriminate…
Content type: Long Read
1. What are the barriers to access safe and legal abortion care?
Abortion is considered a crime in Brazil, except in cases of pregnancy resulting from rape, when it puts the woman's life at risk or, most recently, in cases of fetal anencephaly. Article 273 of the Penal Code also forbids the sale or distribution of medication that is not registered at Anvisa (National Health Agency), which is the case for abortion pills in Brazil. Misoprostol, the active substance of abortive medicines in the…