Advanced Search
Content Type: Long Read
The Investigatory Powers Tribunal (“IPT”) today held that GCHQ hacking of computers, mobile devices and networks is lawful, wherever it occurs around the world. We are disappointed that the IPT has not upheld our complaint and we will be challenging its findings.
Our complaint is the first UK legal challenge to state-sponsored hacking, an exceptionally intrusive form of surveillance. We contended that GCHQ hacking operations were incompatible with democratic principles and human rights…
Content Type: Long Read
Written by Eva Blum-Dumontet
A recent case of lèse-majesté in Thailand (speaking ill of the monarchy) is a worrying example of how Western companies do not just work with governments that fall short of international human rights standards, but can actually facilitate abuses of human rights.
Our investigation on the trial of Katha Pachachirayapong — accused of spreading rumours on the ill-health of the King Bhumibol Adulyadej, thereby causing sharp falls in the Thai stock market — reveal the…
Content Type: Report
In response to the Government publishing proposed new surveillance powers in November 2015, Privacy International submitted this highly detailed analysis to the Science and Technology Committee on the Draft Investigatory Powers Bill in November 2015. Our report proposes significant changes across the Bill to ensure better privacy protection while still enabling public bodies to have the powers they need.
Content Type: Report
Privacy International's new report, For God and My President: State Surveillance in Uganda, exposes the secret surveillance operation and the government's attempts to buy further powerful surveillance tools, including a national communications monitoring centre and intrusion malware, in the absence of a rigorous legal framework governing communications surveillance
Content Type: Long Read
We hate to say we told you so.
Privacy International has for years warned that powerful surveillance technologies are used to facilitate serious human rights abuses with insufficient technological and legal safeguards against abuse.
We now have the most solid evidence to date that we were right. Our latest investigation uncovers disturbing evidence that substantiates our long held concerns.
Today Privacy International publishes an investigation (PDF) into communications surveillance in…
Content Type: Report
Over a dozen international companies are supplying powerful communications surveillance technology in Colombia. Privacy International examines the actors across the world involved in facilitating state surveillance.
The report is available in English and Spanish.
Content Type: Report
For nearly two decades, the Colombian government has been expanding its capacity to spy on the private communications of its citizens. Privacy International's investigation reveals the state of Colombia's overlapping, unchecked systems of surveillance, including mass surveillance, that are vulnerable to abuse.
See the report in English and Spanish.
Content Type: Report
The Pakistani government has significantly expanded its communication interception activities. This Privacy International report covers the intelligence services plan to capture all IP-traffic in Pakistan and other initiatives, pointing to gaps in the laws governing surveillance.
Content Type: Advocacy
This stakeholder report is a submission by Privacy International (PI) and the Right2Know Campaing. PI is a human rights organisation that works to advance and promote the right to privacy and fight surveillance around the world. PI wishes to bring concerns about the protection and promotion of the right to privacy in South Africa before the Human Rights Committee for consideration in South Africa's upcoming review.
Content Type: Report
This report is the result of a collaboration between Privacy International, ARTICLE 19, and the International Human Rights Clinic (IHRC) at Harvard Law School. IHRC conducted desk research as well as interviews with individuals working in civil society organisations in the countries examined. It explores the impact of measures to restrict online encryption and anonymity in four particular countries – the United Kingdom, Morocco, Pakistan and South Korea.
Content Type: Report
This briefing, published on the two-year anniversary of the publication of the first Snowden revelations, warns that governments are looking to maintain and expand mass surveillance, despite the practice being condemned as a human rights violation by courts, parliaments and human rights bodies. It comes on the heels of the adoption of the USA Freedom Act by the US Congress, a solitary and limited example of legislative rollback of surveillance powers since Edward Snowden's revelations began. In…
Content Type: Long Read
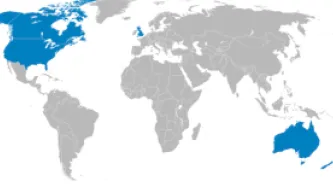
Few revelations have been been as troubling for the right to privacy as uncovering the scope of the Five Eyes alliance. The intelligence club made up of Australia, Canada, New Zealand, the United Kingdom and the United States has integrated its collection efforts, staff, bases, and analysis programs. Yet the legal rulebook governing how the agencies ensure the most comprehensive joint surveillance effort in the history of mankind remains secret.
The little that is known suggests a…
Content Type: Report
Privacy International briefing for the Italian Government on Hacking Team's surveillance exports
Content Type: Report
In this report we present four stories of Moroccan citizens placed under surveillance and the effect it has had on their lives and the lives of their families.
We feel that these stories say a lot about the current context of surveillance in Morocco. We hope they will serve as a medium to foster a much-needed public debate. We also hope that this debate will extend beyond Morocco as we all consider the dangers of unregulated surveillance and surveillance technology around the world.
Content Type: Long Read
As Privacy International celebrates Friday's victory against Britain’s security services - the first such victory this century - we cannot help but feel the success is bittersweet.
After all, we may have convinced the Investigatory Powers Tribunal that GCHQ was acting unlawfully in accessing NSA databases filled with billions of emails and messages, but with a few technical adjustments the intelligence services have managed to insure themselves against any further challenge, at least in…
Content Type: Long Read
Modern day government surveillance is based on the simple concept of “more is more” and “bigger is better”. More emails, more text messages, more phone calls, more screenshots from Skype calls. The bigger the haystack, the more needles we can find.
Thanks to Edward Snowden, we know that this fundamental idea drives intelligence agencies like the NSA and GCHQ - the desire to collect it all, to generate gigantic haystacks through which to trawl. In the almost two years since the first of Snowden…
Content Type: Long Read
Many people imagine intelligence sharing to be a practice whereby men in trench coats silently slide manilla envelopes containing anonymous tip-offs or intelligence reports marked TOP SECRET across tables in smoke-filled rooms.
While such practices certainly exist, they represent only a tiny slice of intelligence sharing activities, and are vastly overshadowed by the massive exchange of bulk unanlysed (raw) intelligence data that takes place between the UK and its Five Eyes allies.…
Content Type: Report
In societies that are in the process of transition towards democracy, democratic control of intelligence organisations is both an indispensable requirement and a pressing need. In many cases, the most serious human rights violations committed by dictatorial governments were intrinsically linked to draconian surveillance and control systems. Systematic spying on trade unions, students and dissident groups was a common feature of 20th-century dictatorships. The persistent violation of citizens’…
Content Type: Report
“Private Interests: Monitoring Central Asia” is a 96-page report detailing its findings from an extensive investigation into electronic surveillance technologies in Kazakhstan, Kyrgyzstan, Tajikistan, Turkmenistan, and Uzbekistan.
The report brings together the findings of PI's team of investigative researchers, consultants, and technical, legal and policy experts, and is the outcome of consultations with confidential sources, regional experts, individuals who have been targeted by…
Content Type: Long Read
Privacy International in October 2014 made a criminal complaint to the National Cyber Crime Unit of the National Crime Agency, urging the immediate investigation of the unlawful surveillance of three Bahraini activists living in the UK by Bahraini authorities using the intrusive malware FinFisher supplied by British company Gamma.
Moosa Abd-Ali Ali, Jaafar Al Hasabi and Saeed Al-Shehabi, three pro-democracy Bahraini activists who were granted asylum in the UK, suffered variously…
Content Type: Long Read
Bad analogies about surveillance technology pervade newspaper reports, politicians’ speeches, and legal arguments. While it’s natural to want simple explanations to understand complex technology, it does us a disservice when governments, the media, or the courts mislead us through analogies that are inadequate. It is even worse if these analogies are used as a basis for policy change.
Privacy International’s legal challenge against GCHQ’s mass surveillance rests…
Content Type: Long Read
Today, Privacy International lodged a legal challenge to GCHQ's extensive and intrusive hacking of personal computers and devices. Below, we answer a few questions about the law underlying our complaint, and why it matters.
Is hacking legal?
As a result of the Snowden revelations, we have learned that GCHQ, often in partnership with the NSA, has been using malicious software to intrude upon our computers and mobile devices.
This type of activity, often called "hacking," is a…
Content Type: Long Read
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re- examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…
Content Type: Report
The recent revelations, made possible by NSA-whistleblower Edward Snowden, of the reach and scope of global surveillance practices have prompted a fundamental re-examination of the role of intelligence services in conducting coordinated cross-border surveillance.
The Five Eyes alliance of States – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the…
Content Type: Report
Privacy International is grateful to the students and staff of the Hebrew University of Jerusalem Faculty of Law Clinical Legal Education Centre, for providing research assistance to this paper.
The advent of new technologies and the Internet have provided new challenges to long-standing human rights norms. By facilitating increased State surveillance and intervention into individuals’ private lives, the spread of digital technologies has created a serious need for States to update their…
Content Type: Long Read
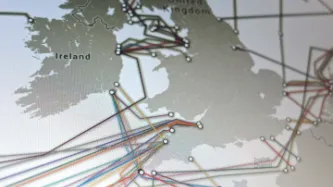
Privacy International filed formal complaints with the Organisation for Economic Cooperation and Development (OECD) in the UK against some of the world’s leading telecommunication companies, for providing assistance to British spy agency GCHQ in the mass interception of internet and telephone traffic passing through undersea fibre optic cables.
According to recent reports, BT, Verizon Enterprise, Vodafone Cable, Viatel, Level 3, and Interoute granted access to their fibre optic…
Content Type: Report
Information technology transfer is increasingly a crucial element of development and humanitarian aid initiatives:
social protection programmes are incorporating digitised Management Information Systems and electronic transfers,
registration and electoral systems are deploying biometric technologies,
the proliferation of mobile phones is facilitating access to increased amounts of data, and
technologies are being transferred to support security and rule of law efforts.
Many of these…
Content Type: Report
New technologies may hold great benefits for the developing world, but without strong legal frameworks ensuring that rights are adequately protected, they pose serious threats to populations they are supposed to empower.
This is never more evident than with the rapid and widespread implementation of biometric technology. Whilst concerns and challenges are seen in both developed and developing countries when it comes to biometrics, for the latter they are more acute due the absence of laws or…
Content Type: Long Read
Britain's spy agency, GCHQ, is secretly conducting mass surveillance by tapping fibre optic cables, giving it access to huge amounts of data on both innocent citizens and targeted suspects, according to a report in the Guardian.
Mass, indiscriminate surveillance of this kind goes against an individual's fundamental human right to privacy. The scope and scale of this program, which monitors the entire British public and much of the world, is neither necessary nor proportionate and thus,…
Content Type: Long Read
Spy agencies have long sought to turn the technologies that improve all our lives against us. From some of the very first forms of remote communications such as telegraph cables, to modern-day means like Skype: if the spies can exploit it, they will.
And, as we’ve learnt over the last few months, the computer and mobile devices that millions of us own and carry around with us every day are no exception to this rule.
The smart phones, laptops, and devices that have changed how we communicate…