Search
Content type: Long Read
Since 2004, October has been designated National Cyber Security Awareness Month in the United States. Many other countries have followed suit, as part of the effort to raise awareness about the importance of cybersecurity, and how we can all work together to improve it.
However, cyber security (or sometimes, just ‘cyber’) has not only become a term with multiple and sometimes contradictory meanings - that go from digital security or digital diplomacy to criminal activities with a digital…
Content type: Advocacy
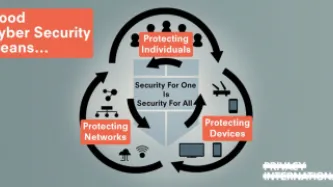
Both “cyber security” and “cyber crime” are terms widely used but often poorly understood. This briefing provides an overview of terminology, concepts and trends in addressing cyber security and cyber crime. It describes the differences between them and associated challenges for the protection of peoples’ security and their human rights. It also highlights key elements and examples from cyber security frameworks and cyber crime legislation globally. The aim is to provide a basis for…
Content type: Long Read
This piece was originally published in Just Security.
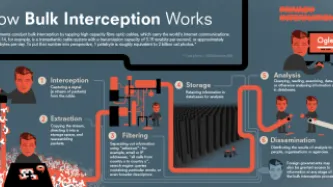
Earlier this month, the European Court of Human Rights issued a major judgment in three consolidated cases challenging the U.K. government’s mass interception program, which was first revealed by Edward Snowden in 2013. That judgment finds notable deficiencies in the legal framework governing mass interception, rendering the program unlawful under Articles 8 and 10 of the European Convention on Human Rights (ECHR), which protect the rights…
Content type: News & Analysis
Today was a big day for the privacy of millions of people. The European Court of Human Rights has today ruled that UK laws enabling mass interception of our communications violate the rights to privacy and freedom of expression. This finding is an important victory for human rights and the rule of law.
The judges found that:
The UK’s historical bulk interception regime violated the right to privacy protected by Article 8 of the European Convention on Human Rights (ECHR) and to free…
Content type: Long Read
The European Court of Human Rights ruled today that the UK government's mass interception program violates the rights to privacy and freedom of expression. The Court held that the program "is incapable of keeping the 'interference' to what is 'necessary in a democratic society'". This finding is an important victory for human rights and the rule of law. Below, we break down the key parts of the decision.
The Court's ruling comes after a five-year battle against two UK mass surveillance…
Content type: Press release
The European Court of Human Rights has today ruled that UK laws enabling mass surveillance violate the rights to privacy and freedom of expression.
Judges found that:
The UK’s historical bulk interception regime violated the right to privacy protected by Article 8 of the European Convention on Human Rights (ECHR) and to free expression, protected by Article 10.
The interception of communications data is as serious a breach of privacy as the interception of content, meaning the UK…
Content type: News & Analysis
Our intervention comes on the back of mounting evidence that the South African state’s surveillance powers have been abused, and so-called “checks & balances” in RICA have failed to protect citizens’ constitutional right to privacy.
Among our core arguments are:
That people have a right to be notified when their communications have been intercepted so that they can take action when they believe their privacy has been unlawfully breached. Currently RICA prevents such notification, unlike…
Content type: News & Analysis
Photo was found here
This essay was published in The Sur International Journal of Human Rights, Issue 27, July 2018.
Abstract:
This essay focuses on elections in Kenya and analyses the use of technology and the exploitation of personal data in both the electoral process and campaigning. We only need to look to Kenya’s election history to understand why it is important. The 2007/2008 election resulted in violence that killed over 1,000 people and displaced over 600,000. The 2013 election was…
Content type: Advocacy
This photo originally appeared here.
For years, Privacy International and our partners in Kenya have been promoting the right to privacy in Kenya through research and investigations into government and private sector policies and practices and advocating for the adoption and enforcement of the strongest data protection and privacy safeguards.
The need for Kenya to adopt a comprehensive data protection framework (in addition to strengthening privacy protections in other legislation) has always…
Content type: News & Analysis
As the international cyber security debate searches for new direction, little attention is paid to what is going on in Africa. Stepping over the remains of the UN Group of Governmental Experts, and passing by the boardrooms of Microsoft struggling to deliver their Digital Geneva Convention, African nations are following their own individual paths.
Unfortunately, these paths increasingly prioritise intrusive state surveillance and criminalisation of legitimate expression online as…
Content type: News & Analysis
In order to uphold the law and keep us safe, the police can seriously interfere with a range of fundamental human rights. And so transparency and public scrutiny of their actions are essential to protect against misconduct and abuse.
So why is the National Police Chiefs’ Council (NPCC) now permitted to operate in secret?
We all have the right to seek information from most public bodies – including the police – under the Freedom of Information Act (FOIA) 2000. When the law was first…
Content type: Advocacy
Tanto la privacidad como la seguridad son esenciales para proteger a los individuos, su autonomía y su dignidad. El detrimento de la privacidad implica el detrimento de la seguridad de los individuos, sus dispositivos y la infraestructura de la que forman parte. La gente necesita privacidad para sentirse libremente segura y proteger su información, así como para gozar plenamente de otros derechos.
Una cantidad cada vez mayor de Gobiernos en el mundo está recurriendo también al hackeo para…
Content type: News & Analysis
Actualmente, las empresas tecnológicas se encuentran inmersas en constante cambio. Uno de ellos es la creciente importancia que ha cobrado la seguridad digital, convirtiéndose en una prioridad. Que un emprendimiento resguarde su seguridad digital significa que puede gestionar los riesgos asociados a mantener la confidencialidad, integridad y disponibilidad de su información.
En este contexto, resulta de gran relevancia que las personas responsables del emprendimiento digital y el…
Content type: News & Analysis
El objetivo es facilitar a la sociedad civil una guía para la navegación de este organismo, efectuar un diagnóstico que permita situar cualquier persona interesada sobre la actualidad de la temática a nivel regional y descubrir la agenda de seguridad digital que sostiene la OEA en el continente.
Finalmente, concluimos con una serie de breves recomendaciones dirigidas a los organismos de la OEA. Con ello, esperamos que este órgano reconozca el papel que puede jugar como catalizador en el…
Content type: Advocacy
Privacy and security are both essential to protecting individuals, including their autonomy and dignity. Undermining privacy undermines the security of individuals, their devices and the broader infrastructure. People need privacy to freely secure themselves, their information, and fully enjoy other rights.
A growing number of governments around the world are embracing hacking to facilitate their surveillance activities. When governments hack for surveillance purposes, they seek to…
Content type: News & Analysis
Nota de prensa
Peruanos rutinariamiente otorgan y son sometidos a verificación de sus datos personales y biométricos (huella digital, retina) en entidades públicas y privadas sin ser informados claramente de la finalidad y tratamiento posterior de la información.
RENIEC ocupa un rol predominante dentro del ecosistema nacional para dotar de coherencia al sistema de identificación que emplea tecnología biométrica. Sin embargo, pese a contar con diferentes estándares y medidas de seguridad en el…
Content type: Long Read
The European Union's new data privacy law (General Data Protection Regulation, better known as GDPR) takes effect today May 25th, 2018, after a two-year transition period. Despite some companies appearing to believe otherwise, and many articles misrepresenting its contents, the GDPR will have a significative impact beyond the European Union, and it will extend many of its data privacy safeguards to users’ data globally.
There are a number of reasons that explain this impact:
Obligations…
Content type: News & Analysis
En el 2011 se liquidó el DAS. Las violaciones, excesos y abusos de la inteligencia estatal que comenzaban por la intimidad y terminaban con la vida de los ciudadanos habían producido condenas judiciales a varios exdirectores: claro indicador de que se necesitaba un cambio. Siete años ha tenido el Estado colombiano para ordenar la casa y esta semana someterá sus récords de derechos humanos al examen de los miembros de Naciones Unidas. La evaluación analizará, entre otros…
Content type: News & Analysis
Los frecuentes escándalos sobre el abuso de la vigilancia estatal en actividades de inteligencia, la exagerada obligación legal que tienen las empresas de telefonía de retener los datos de las comunicaciones de sus usuarios por cinco años o la manera como se diluye el concepto de privacidad en el Código de Policía serán parte del examen que se haga en el seno de la ONU sobre la forma como Colombia cumple sus compromisos de derechos humanos.
Dirigido por los Estados y con el auspicio del…
Content type: News & Analysis
In the lead-up to the 30th session of the Universal Periodic Review which took place on 10 May 2018, Fundación Karisma, a partner organisation in the Privacy International Network, joined a coalition of civil society groups in Colombia to raise more awareness about the country's human rights record.
As part of the joint effort, the coalition produced factsheets on various human rights in the Colombian context, including the right to privacy. It is available in both English and Spanish.
Content type: Report
The use of biometric technology in political processes, i.e. the use of peoples’ physical and behavioural characteristics to authenticate claimed identity, has swept across the African region, with 75% of African countries adopting one form or other of biometric technology in their electoral processes. Despite high costs, the adoption of biometrics has not restored the public’s trust in the electoral process, as illustrated by post-election violence and legal challenges to the results of…
Content type: Report
La seguridad digital es una discusión crítica y hay que reconocer que la sociedad civil y los grupos de interés público no han sido suficientemente considerados. Como respuesta, varias organizaciones de la sociedad civil de América Latina se unieron para presentar informes que recuerdan a las entidades estatales responsables de formulación de políticas públicas que la seguridad digital debe tener en cuenta la seguridad de las personas y los derechos humanos. Presentamos la serie, Derechos…
Content type: Long Read
As we said before, Facebook and Cambridge Analytica scandals are a wake-up call for policy makers. And also a global issue. People around the world are concerned by the exploitation of their data. The current lack of transparency into how companies are using people’s data is unacceptable and needs to be addressed.
There is an entire hidden ecosystem of companies harvesting and sharing personal data. From credit scoring and insurance quotations to targeted political communication, this…
Content type: Long Read
Today Privacy International together with 27 other organisations from across Europe urge European governments to strengthen the protection of privacy and security of online communications. The proposal to reform e-privacy in Europe was launched in January 2017. However, despite the clear and urgent need of this reform, recently demonstrated by the Facebook/Cambridge Analytica case, the negotiations by EU member states have been inconclusive. Worse still, some governments seem willing to…
Content type: News & Analysis
Written by Karisma Foundation
7:03: Catalina leaves her apartment and a security camera follows her down the hall, another one observes her in the elevator while she fixes her hair. As she exits the building, the warden tells her she doesn’t have to fix her hair because she is already pretty as she is. She gets to the parking lot where another two cameras look at her while she gets into her car.
8:00: She is heading to an open data workshop organized by the Colombian government in a…
Content type: Long Read
To mark International Women’s Day 2018, Privacy International and some of our partner organisations - Datos Protegidos, Derechos Digitales, the National Coalition for Human Rights Defenders-Kenya, the Karisma Foundation, and the Foundation for Media Alternatives – are telling the stories of women across the world as told by their data over the next seven days (for us, it’s International Women’s Week!).
Gender inequality has many complex dimensions and data exploitation is yet another.…
Content type: News & Analysis
Written by Privacy International
07:06: Camille’s smart pillow sends a signal to her smartphone that it’s time for her to wake up. She checks the quality of sleep on the app – last night was not great. Because the pillow tracks the motion in her bed, the company knows what else she may (or may not) have been up to. But the company doesn’t just track her when she is in bed. By downloading the app, Camille has also authorised access to her location wherever she goes, her camera, her contact…
Content type: News & Analysis
Written by the Foundation for Media Alternatives
7:01: Naomi wakes up and gets ready for the day.
7:58: Naomi books an Uber ride to Bonifacio Global City (BGC), where she has a meeting. She pays with her credit card. While Naomi is waiting for her Uber, she googles restaurant options for her dinner meeting in Ortigas.
9:00: While her Uber ride is stuck in traffic on EDSA (a limited access highway circling Manilla), Naomi’s phone automatically connects to the free WiFi offered by the…
Content type: News & Analysis
Written by Datos Protegidos
04:16: Carolina can´t sleep. She grabs her mobile from the nightstand next to her bed to check her WhatsApp notifications and read some tweets. She decides to disconnect to and tries to go back to sleep.
07:00: Carolina is woken by her mobile phone alarm. She picks it up and checks her social networks and messages again. To her astonishment, she finds a message in a WhatsApp group from her former college classmate Pablo at 5:25 asking if anyone was still…
Content type: News & Analysis
Written by Derechos Digitales
03:00: Maritza wakes up and gets ready. It’s still dark. She has to go stand in a queue outside the nearest grocery store, where after several hours her fingerprint will be scanned to retrieve her personal information from a governmental database. This will tell the cashier not only her address, full name and phone number, but also if she already bought her allotted ration of food that month. If so, she will be sent back empty-handed. There are drones flying…